CrushFTP can operate in a restricted environment where a front end DMZ server processes protocols and connections, and a secured internal server has access to the file system, database, or other protected resources.
1.) To start a DMZ instance waiting for its configuration from the internal server:
java -jar CrushFTP.jar -dmz 9000 java -jar CrushFTP.jar -dmz 9000 192.168.1.10,10.0.1.5,192.168.1.11If you specify acceptable IPs, and the IP isn't int he list, the connection is dropped, and a message logged.
2.) Now that the server is configured, you need to configure prefs for this server. Its usually easiest to start with your existing prefs on your internal server and adjust it later on.
So duplicate prefs.XML and call it "prefs_dmztest.XML". The "_dmz1" is part of a specific naming scheme. This server will be identified as "dmztest". So if you wanted another name such as 'extra' you would do "prefs_extra.XML".
3.) Now that the prefs are ready, lets configure the port in CrushFTP that will attach to the DMZ instance and handles things.
Create a new port item, set its protocol to be DMZ:// and configure the IP and port for the DMZ server where the core will be connecting out to the DMZ. The IP is the IP of the DMZ server and the port is the port you used above when you started it. The 'name' field that would normally be optional is required here as that is how it identified what prefs.XML file to use. So the name should match that second part of the filename you made above. In this case 'dmztest'.
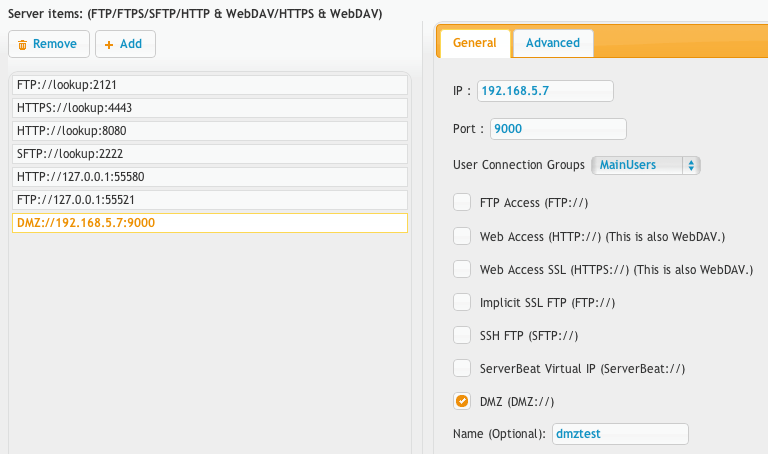
4.) Now when you go back to the Server Admin tab, you will notice a new drop down selector to the right of the tabs allowing you to control the instance you are managing. Select your DMZ instance. If the interface loads, then it means the DMZ server is communicating correctly. Now we need to setup the forwarding user.
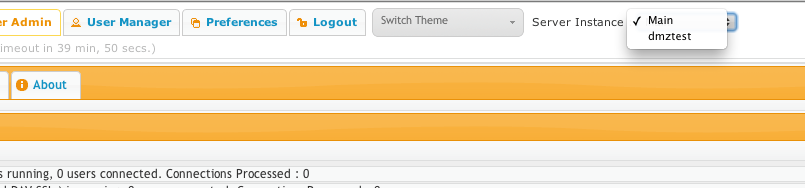
5.) Go to the user manager on the DMZ instance. Create a new user named "template". No need for a password as its not used. This is a reserved username that forwards to an internal server.
Create a new remote item using the third button down in the middle of the virtual file system area. Configure it exactly as shown in the screenshot. Don't change the IP or port, just leave it as the screenshot shows. Then give it full permissions with the checkboxes on the left after you save.
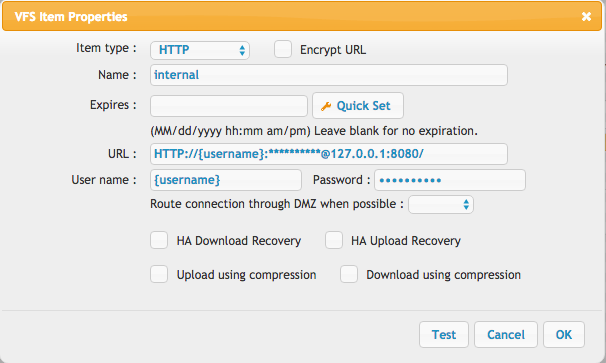
Since this is a DMZ server, this remote item will be used by the DMZ to talk to the internal server. It will adjust the IP, port, and fill in the user/pass info as needed dynamically.
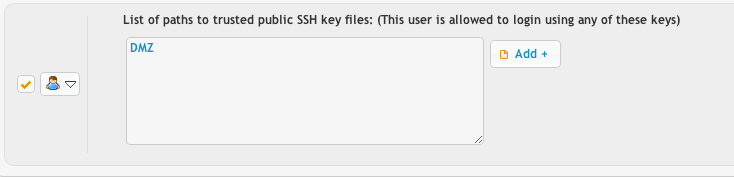
If the DMZ will do public key authentication, in the user manager, set the public key path for this 'template' user to be just the three letters in uppercase: DMZ. This will allow automatic public key verification based on keys configured on the internal server to be validated on the DMZ as well.
When a connection comes into the DMZ server over SFTP/FTP(es)/HTTP(s)/WebDAV(s), the DMZ server talks to the internal server on an existing connection it already has from the internal server. This communication is over a SSL socket always initiated from the internal to the DMZ. The protocol the DMZ then uses inside this secure connection is HTTP. The internal server then attaches the connection to the first HTTP (not HTTPS) port internally that it finds in its list of ports.
So all interaction between DMZ and Internal is the HTTP protocol (inside a SSL connection). The user may be using SFTP to connect to the DMZ, and ask for a directory listing. This then results in the DMZ asking the internal server for a dir listing using HTTP, and then its translated and delivered to the SFTP client as a SFTP dir listing. This way all protocols are handled by the DMZ, and the internal server does everything using one protocol that can handle everything.
No prefs are stored on the DMZ server.#
No users are stored on the DMZ server.#
No user data files are stored on the DMZ server.#
File transfers are streamed through to the Internal server.#
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
dmz_port.png | 54.9 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
dmz_publickey.png | 13.9 kB | 1 | 29-Dec-2020 05:25 | Ben Spink | |
png |
dmz_selector.png | 30.3 kB | 1 | 29-Dec-2020 05:25 | Ben Spink | |
png |
dmz_user.png | 57.6 kB | 3 | 29-Dec-2020 05:25 | Ben Spink |
