This plugin allows us to integrate CrushFTP with your LDAP server, such as the Microsoft Active Directory server, or OpenLDAP, etc.
The settings can be grouped into three major sections, based on functionality:
1. Connectivity settings#
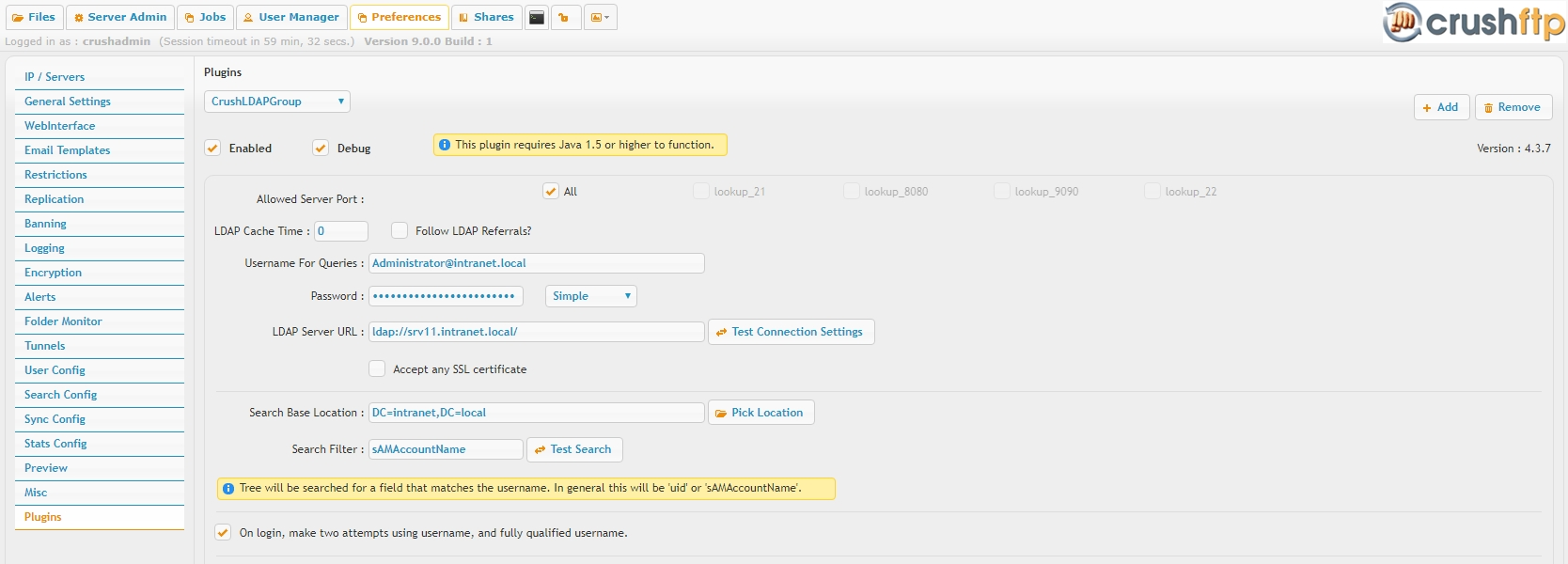
LDAP server URL, fully qualified user name and password of an LDAP account used for queries. The account needs read only access on the full LDAP tree. The plugin supports referral chasing, in case of multiple forests with trust relationship between, can allow this by setting the Follow referrals option.
To use a secure LDAP (ldaps://) URL, set either the Accept any SSL certificate option or import the LDAP server public certificate into the Java trust store, cacerts.
Multiple server URLs supported, for high availability, the plugin will round robin between these, need to enter those as comma separated list.
The plugin also allows multiple instances, this feature facilitates integration with different user domains or to have different configurations to catch a certain subset of users, etc. The query order is left to right, as the instances appear on the tab list. First successful hit allows login, we look for the user no further.
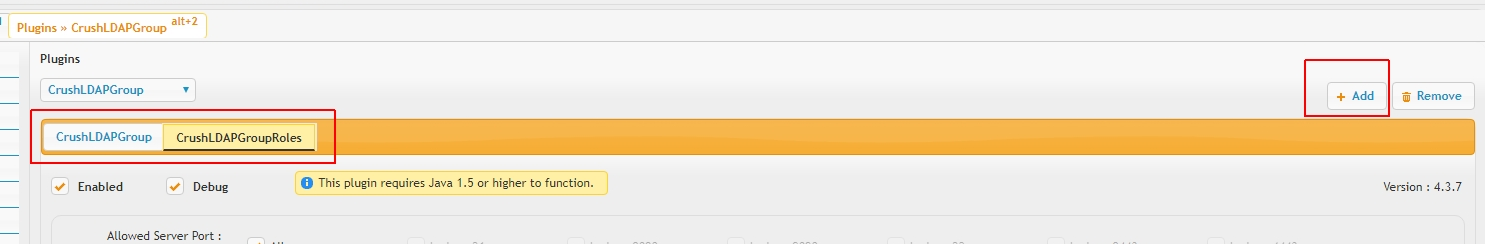
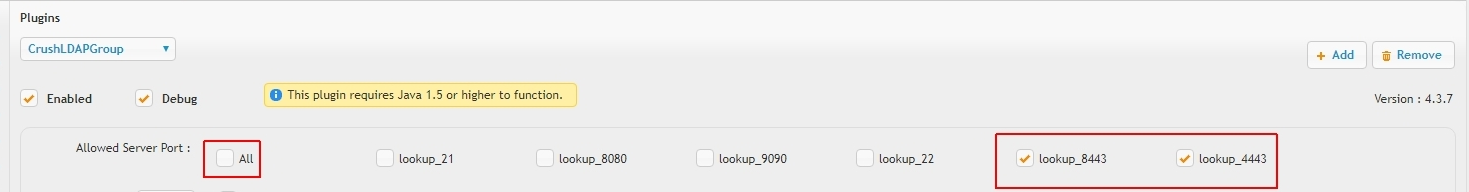
Each plugin instance can restrict the allowed users to certain server ports or Sever Connection Groups
2. LDAP user lookup#
Search base location:#
This field needs to be pointed to the root of the LDAP tree or full path to some container OU. LDAP objects outside this path will not be visible to the plugin.Search filter:#
This field needs to contain some unique LDAP attribute name, like sAMAccountName for plain username or userPrincipalName for the user FQDN as allowed username format. We can also automatically round robin between these if the On login, make two attempts... option is enabled. This field also allows more complex LDAP filter expressions , an example for enabled user accounts only(&(objectClass=user)(objectCategory=person)(sAMAccountname=?)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))
Lookup parameters:#
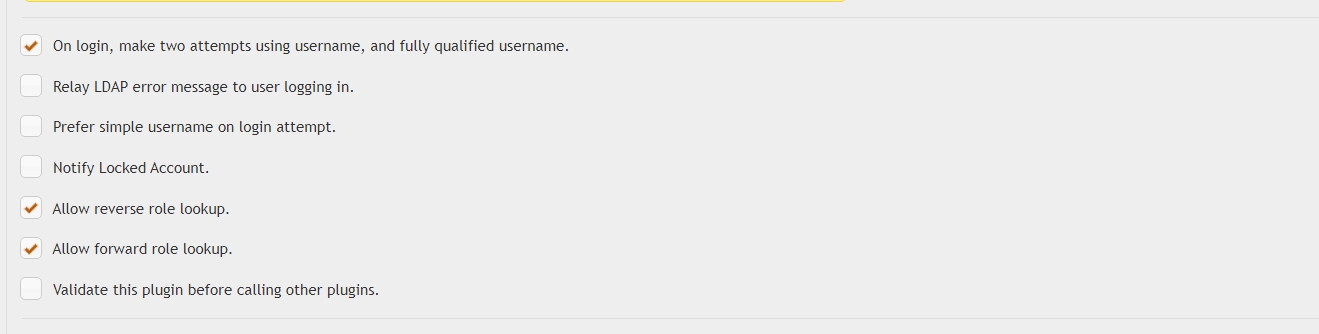 |
- On login, make two attempts using username, and fully qualified username
- try to look up the user by both it's FQDN and it's plain user name. This allows to log in by plain username (sAMAccountName) even if the Search Filter is set to userPrincipalName
- Relay LDAP error message to user logging in
- in case of access denied, show the LDAP error in the Webinterface or client application along with our standard error message
- Prefer simple username on login attempt
- prioritize user lookup user by it's sAMAcountName if the Search Filter is set to anything else
- Notify Locked Account
- If an account becomes disabled or locked, this option triggers sending an email to the LDAP User's email address.
- Allow reverse role lookup
- validate role membership by checking the user's memberOf attribute against the roles list
- Allow forward role lookup
- validate role membership by checking all roles' member attribute for the user DN
- Validate this plugin before calling other plugins
- in case multiple integration plugins are linked together, call the LDAP plugin first ( for example in case of RADIUS & LDAP )
Roles and inheritance#
Roles allow filtering on LDAP group membership. Each role has two options, a role filter and an optional role template field. Each role filter needs to be set a full LDAP path to a security group as of the user object's memberOf attribute value.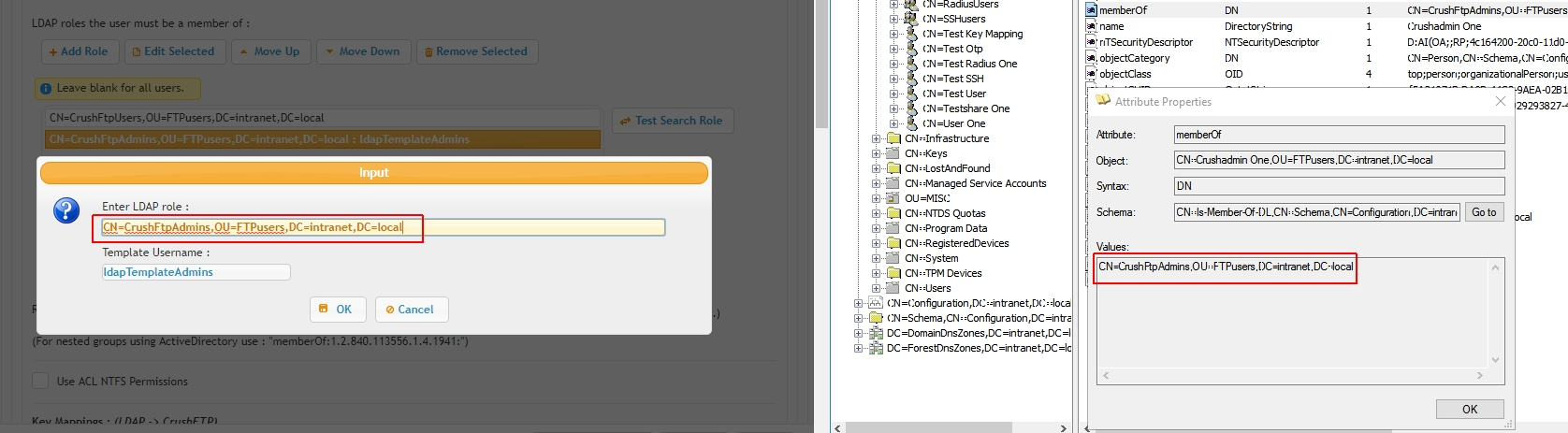
A role template is a local CrushFTP user account for parenting group membership based inheritance. In case such a role template is assigned, all LDAP users member of this group will inherit settings from this account, including it's VFS configuration; this can be used to grant per group based common working directories or local admin rights for example.
A master template can also be designated , with instance wide scope

3. Home folder access#
Most important, as the user will be denied login in case of an invalid home directory configuration.
LDAP used for authentication only#
With this option if is enabled, the plugin will match the logging in user name against the local user database, in case of a successful match, the user is allowed to log in with it's LDAP password, and the user settings, including it's VFS configuration, is loaded from the local account. This method allows the most fine grained control over each LDAP integrated account, with the cost of being tedious, will need to create for each allowed user a matching account in User Manager manually (with blank or random password, since that will be ignored anyways).
LDAP home directory or local home directory#
This method is used if the above option is not enabled. The plugin will attempt to grant the user folder access to a path loaded from an LDAP attribute value or assign a local folder path. In this case local doesn't necessarily means a local folder on the CrushFTP server host itself, we do support network share access via UNC paths or any of the supported remote networking protocols based URLs (FTP, SMB, etc.).HomeDirectory field#
If this contains a valid LDAP attribute name, the plugin will attempt to grant access to the path contained by the attribute as it's value. In case of Microsoft Active DIrectory, this field should be set to homeDirectory, in case of Linux SLAPD, to unixHomeDirectory, etc. or any arbitrary LDAP attribute containing a single folder path or coma separated list of paths. To disable, set this field value to NA (or any arbitrary value not matching an LDAP attribute name).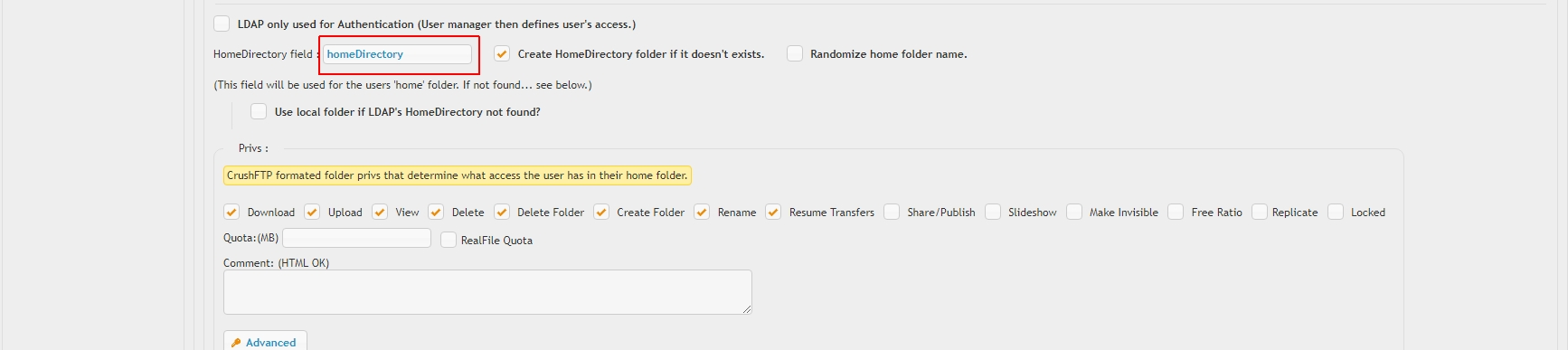
Use local folder if LDAP's HomeDirectory not found#
In case this option is enabled, and loading a valid path as per above section config, failed, the plugin will attempt to grant local folder access within a root folder pointed to by the Path field value. Set the Append username to path and Create folder with username to create individual, username based home directories. A more advanced use case is to honor ACL permissions using an SMB:// URL and server variables to dynamically reference user credentials at login time
SMB3://INTRANET{backslash}{username}:{password}@srv11.intranet.local/SHAREROOT/
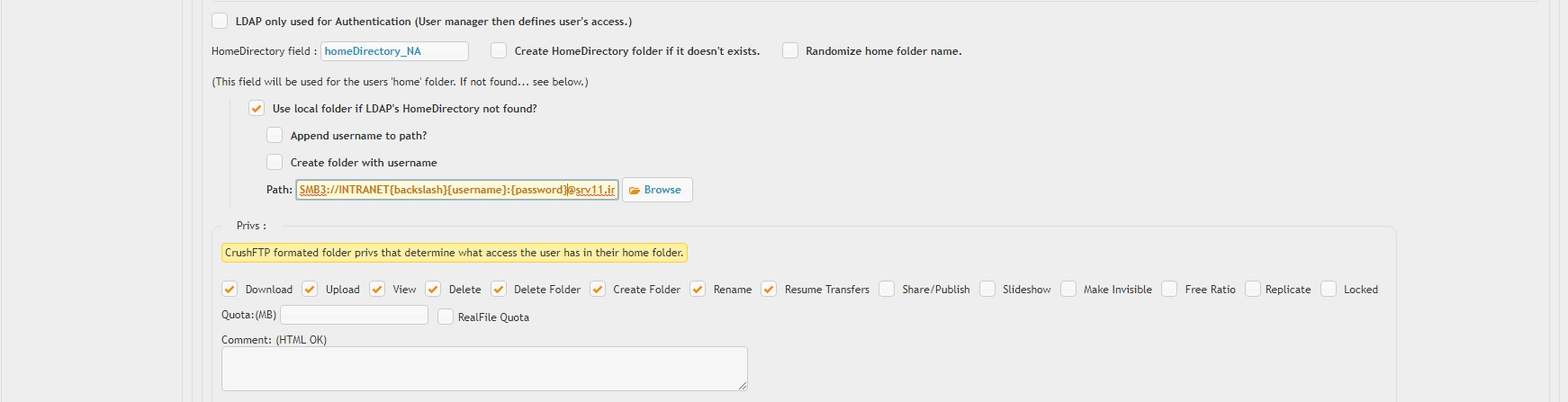
The Create additional subfolders in home directory : section instructs the plugin to automatically create a pre defined set of subfolders below the user's home directory root.
In stream PGP file Encryption and Sync can be configured using the Advanced menu.
4. Key mapping#
This section allows mapping of LDAP attributes to local user parameters. Most common use case LDAP integration with SSH user public key based authentication. In this case, an otherwise redundant LDAP field, description was used to store the user public key path (or the key file content). IMPORTANT: LDAP user email address is automatically mapped behind the scenes. This works with most LDAP implementations, we do an implicit mapping of the LDAP user's mailattribute value to our specific user_email user attribute. Need only to map manually in case of some non-standard LDAP implementations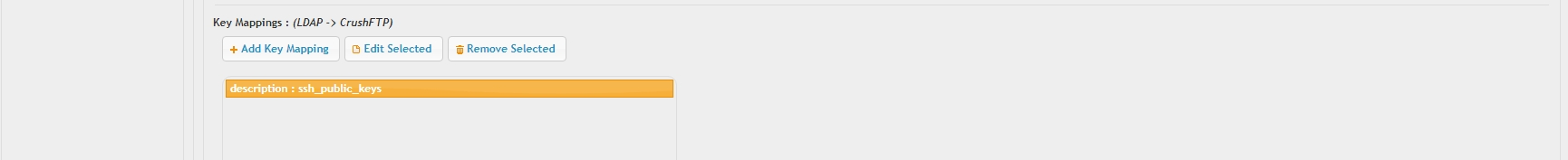 .
.
Troubleshooting#
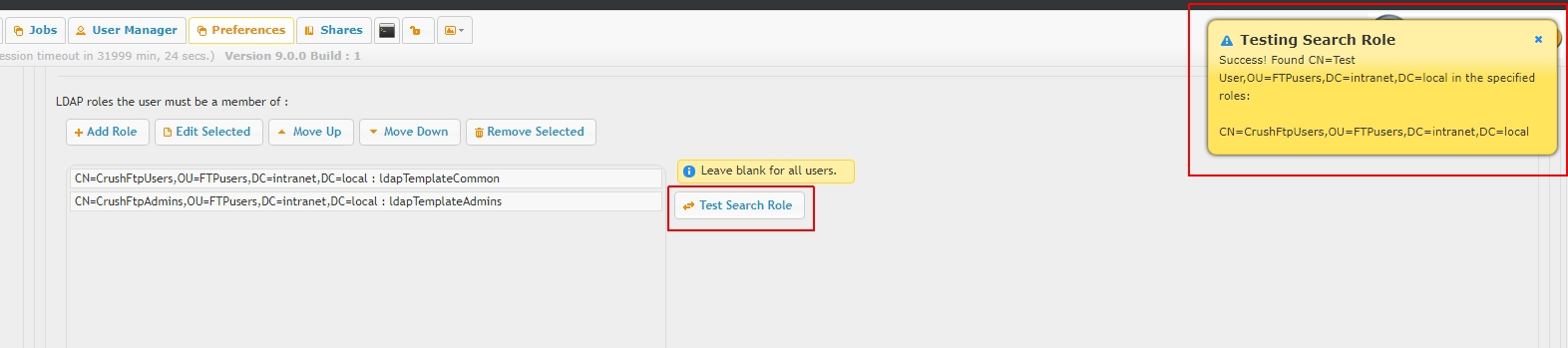
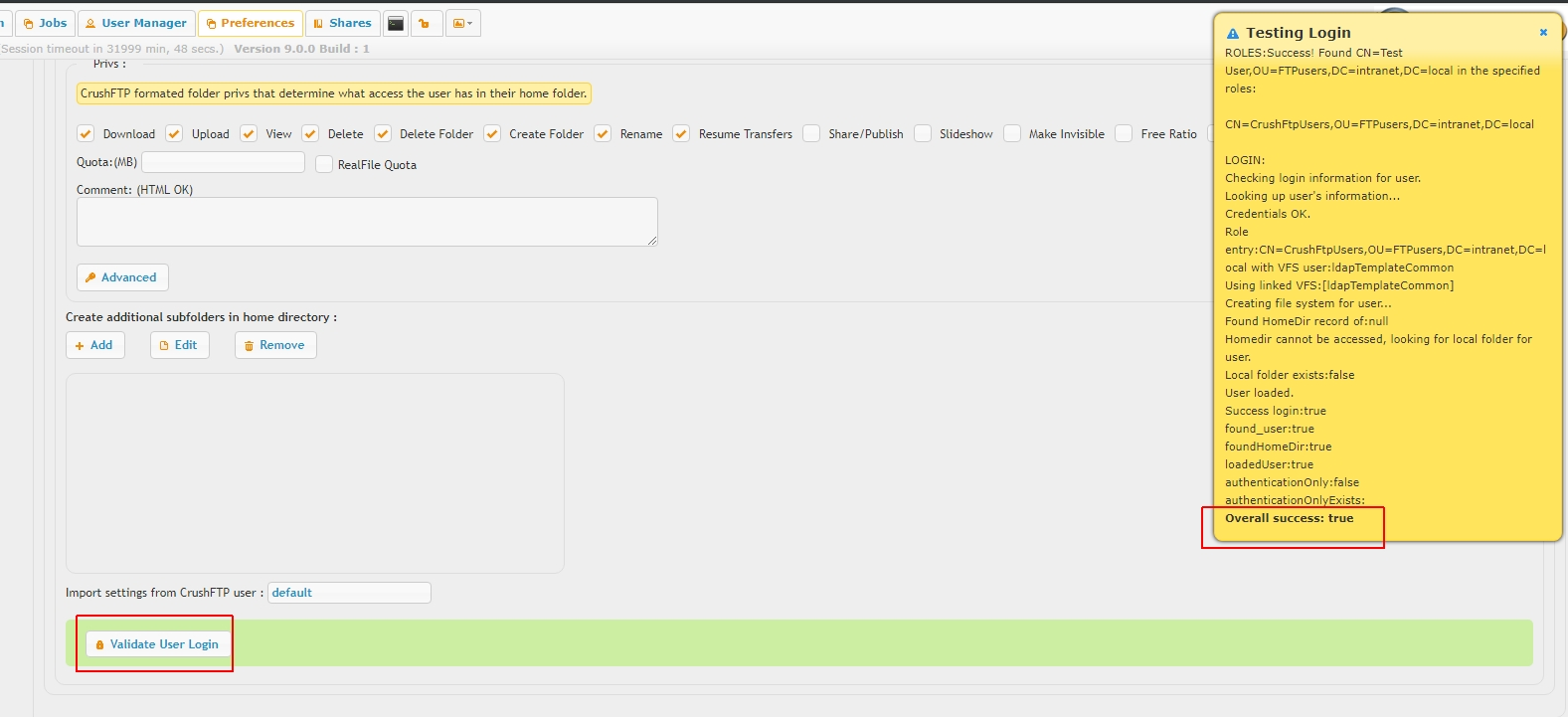
There are separate test tools to validate connectivity and query account credentials
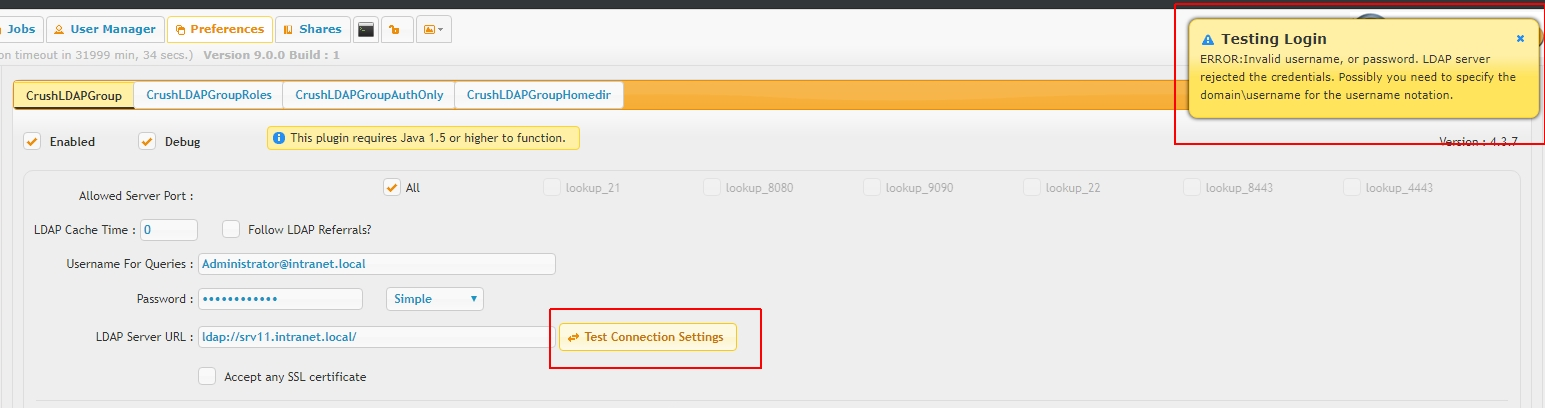
user lookup and role based filtering
and user login (without the need of the actual end user password, the test tool will fake a login based on user lookup and validate home folder access)
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
jpg |
Clipboard01.jpg | 219.8 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | uru |
png |
Clipboard01.png | 207.7 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
Notify_Locked_Account.png | 4.7 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
crushldapgroup1.png | 68.3 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
crushldapgroup2.png | 40.8 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
homedir0.png | 16.4 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
homedir1.png | 111.3 kB | 2 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
homedir2.png | 134.0 kB | 2 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
ldapconn1.png | 207.7 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
ldapconn2.png | 50.6 kB | 2 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
ldapconn3.png | 60.1 kB | 2 | 29-Dec-2020 05:25 | Ada Csaba | |
jpg |
ldaplookupsettings1.jpg | 66.1 kB | 1 | 19-May-2021 18:08 | Ada Csaba | |
png |
mapping1.png | 25.1 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
roles1.png | 271.1 kB | 3 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
roles2.png | 6.2 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
trblshoot1.png | 144.8 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
trblshoot2.png | 113.0 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba | |
png |
trblshoot3.png | 230.8 kB | 1 | 29-Dec-2020 05:25 | Ada Csaba |
