To configure AS2/3, you need to have a user configured in the UserManager, and a job that does the AS2 without any copy or move task, all the task that have to be done are
Notice there is no copy or move operation there. The AS2 item is the special protocol that does that type of activity. When the remote server sends a MDN, it comes into an account you have setup for this...and that AS2 task above will be handed that MDN response internally inside CrushFTP so it knows the response came back.
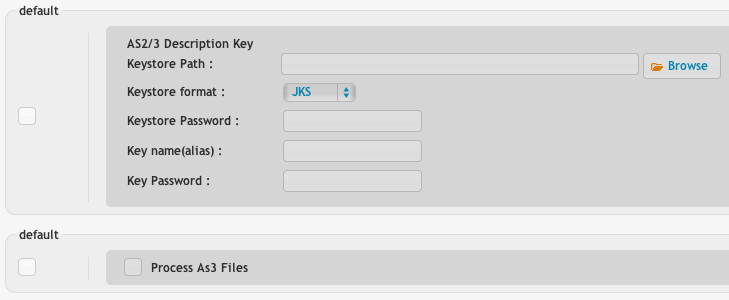
If the remote company is just sending you a file (not a MDN) it also comes in through an account in CrushFTP. In CrusHFTP's User Manager, you can make accounts, and on each account you can configure the AS2/3 information to use. This is the information that will be used to decode and decrypt incoming HTTP transfers that are in AS2 format. This account could also be used for normal FTP/SFTP/HTTP transfers too, but if you have the AS2 stuff configured, that info is used to decode and decrypt the AS2 data, and for sending a MDN reply back to the partner who sent you the file.
For beginning you should have a FindTask in the job. A FindTask, that is searching for the folder contains the data that should be sent using AS2.

For the second step, you have to exclude the files that are already encrypted.
After that is done, you should exclude the MDN responses that you already have.
Make sure you have the certificate of the AS2 receiving machine added as a trusted certificate in the certificate chain that you use.
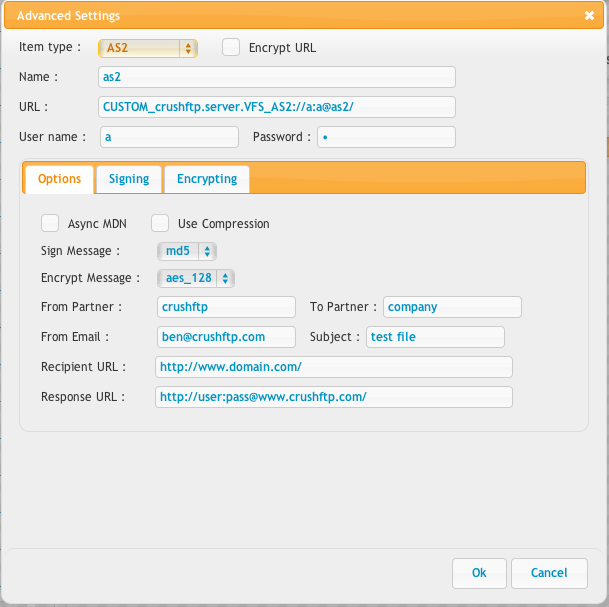
On the AS2 task you have to set it like:
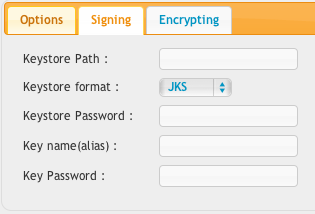
If you have your partner's public key for who you want to send to, you need to import that into a keystore file.
keytool -importcert -alias {partner_name} -file {partner_public_key_file} -keystore {partner_name}.jks
That will be the keystore you use for the encryption tab. {partner_name}.jks
For signing, and your public key you are going to give your partner...
keytool -genkeypair -alias {your_name} -keyalg RSA -keysize 1024 -keystore {your_name}.jks
Then get your public key out to give to your partner:
keytool -export -alias {your_name} -file {your_name}.cer -keystore {your_name}.jks
Send them the resulting {your_name}.cer file. That is your public key they can encrypt with. You set this keystore file {your_name}.jks on the "AS2/3 Decryption Key" panel of the user manager and on the signing tab of the VFS item.
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
Encrypt.png | 78.1 kB | 2 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
Screen Shot 2013-11-23 at 1.35... | 30.3 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
Screen Shot 2013-11-23 at 1.37... | 72.2 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
as2_options.png | 55.7 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
as2_receive.png | 25.8 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
as2_signing.png | 17.1 kB | 2 | 29-Dec-2020 05:25 | Ben Spink | |
png |
complete.png | 158.7 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
delete.png | 49.4 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
exclude1.png | 42.0 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
exclude2.png | 41.1 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
find.png | 92.8 kB | 4 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
new_vfs.png | 3.6 kB | 1 | 29-Dec-2020 05:25 | Ben Spink | |
png |
options.png | 135.7 kB | 2 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
signing.png | 76.2 kB | 2 | 29-Dec-2020 05:25 | Halmágyi Árpád | |
png |
tasks.png | 47.0 kB | 1 | 29-Dec-2020 05:25 | Halmágyi Árpád |
