1. Sharepoint Microsoft Graph REST API-based integration.
#
More info about Microsft Graph REST API: https://learn.microsoft.com/en-us/graph/api/resources/onedrive?view=graph-rest-1.0}

Remote item name: Sharepoint
!!! Proxy Configuration: If your server accesses the internet through a proxy, make sure to whitelist the following domains to allow authentication and Microsoft Graph API access:
• login.microsoftonline.com
• graph.microsoft.com
Open the Microsoft Azure Portal: https://azure.microsoft.com/en-us/features/azure-portal
 /
/Application registration: Navigate to App registrations in the Azure Portal. Click on "New registration" to create a new application.
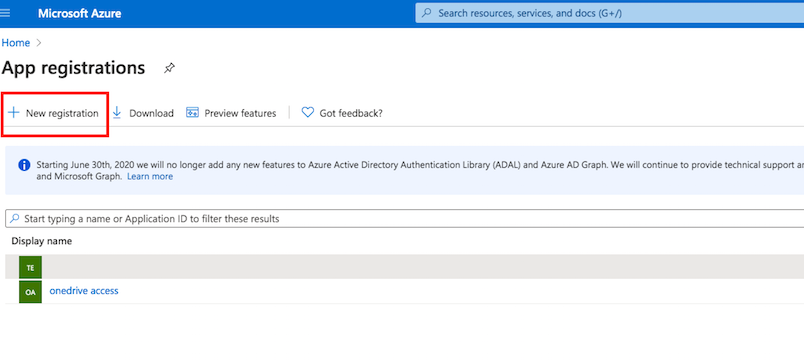
The Redirect URL must end with "register_microsoft_graph_api/".
http://localhost:9090/register_microsoft_graph_api/
or
https://your.crushftp.domain.com/register_microsoft_graph_api/
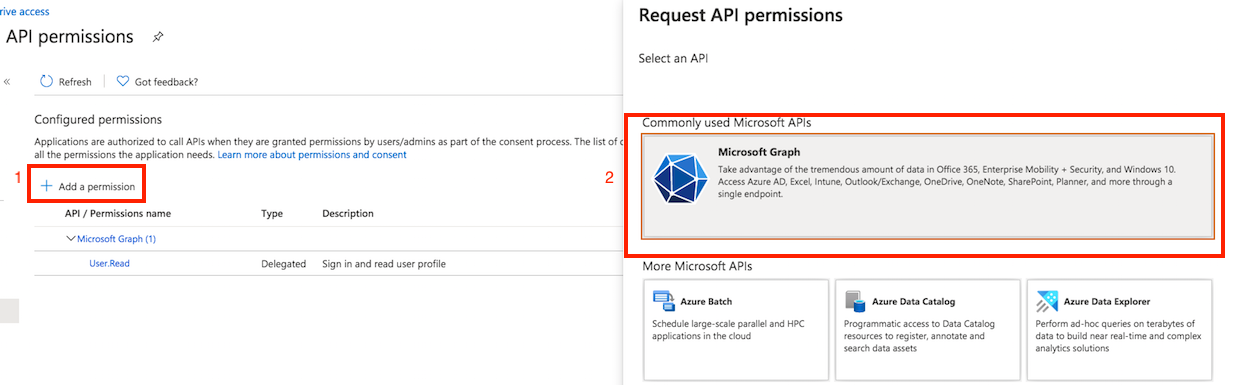
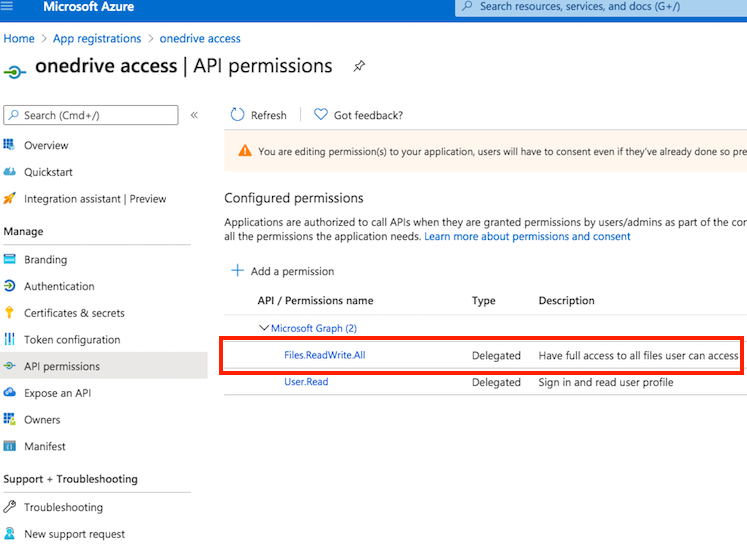
Configure API permission: You must also grant permissions for Microsoft Graph. Go to the API Permissions section, click Add a permission, and select Microsoft Graph. To learn more about Microsoft Graph permissions—including the difference between Application and Delegated permissions—refer to the official documentation: https://learn.microsoft.com/en-us/graph/permissions-overview?tabs=http

1.1 Application Permission:
#
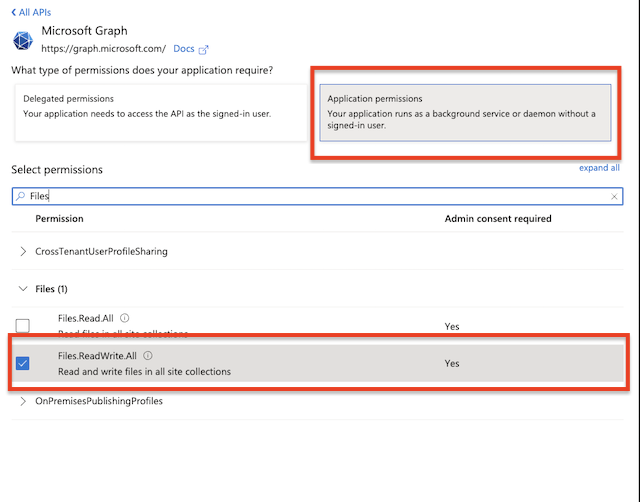
a.) Files.ReadWrite.All: Grants the application read and write access to all files the signed-in user can access, across all user drives and document libraries (including SharePoint sites and OneDrive for Business).
This includes the ability to:
• List, read, update, create, and delete files and folders
• Upload/download documents
• Modify file metadata
Configure API Permission: Navigate to API Permissions. Click on Add a permission button. Select Microsoft Graph. Then select Application Permission. Search for Files and check the flag Files.ReadWrite.All permission.
b.) Sites.FullControl.All: Grants the application full control over all site collections in the tenant without user interaction. ( More info -> https://learn.microsoft.com/en-us/graph/permissions-reference#sites-permissions
 )
)This permission allows the app to:
• Read and write all files in all SharePoint Online site collections
• Manage lists, document libraries, subsites, and site permissions
• Perform site-level actions across the entire tenant
Configure API Permission: Navigate to API Permissions. Click on Add a permission button. Select Microsoft Graph. Then select Application Permission. Search for Sites and check the flag Sites.FullControl.All permission.
c.) Sites.Selected: Grants the application no access to SharePoint sites by default. However, you can explicitly grant access to specific sites by using the Microsoft Graph API.
Configure API Permission: Navigate to API Permissions. Click on Add a permission button. Select Microsoft Graph. Then select Application Permission. Search for Sites and check the flag Sites.Selected permission.
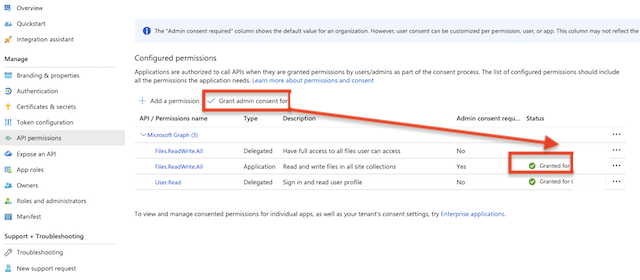
Grant Admin consent for the newly added permission.
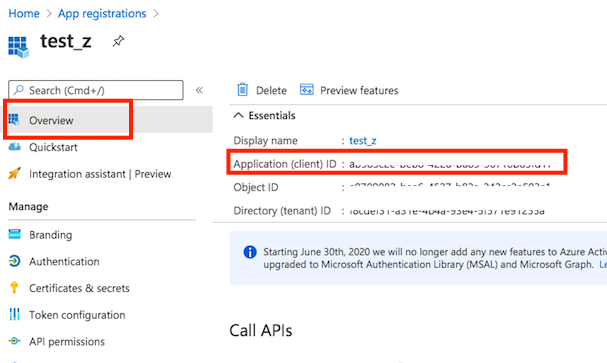
Client id : You can find it at Azure portal -> App Registration -> Overview:
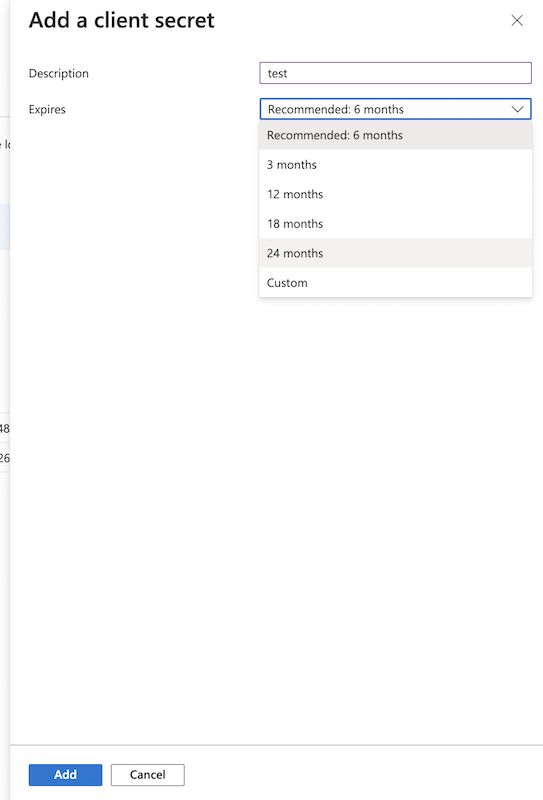
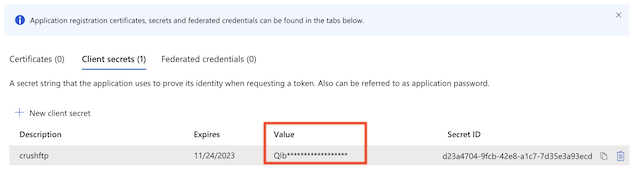
Secret key: A new client secret needs to be created as well. Go to the "Certificate & secrets" and generate a new secret key. Click on New client secret.
Authentication related settings:
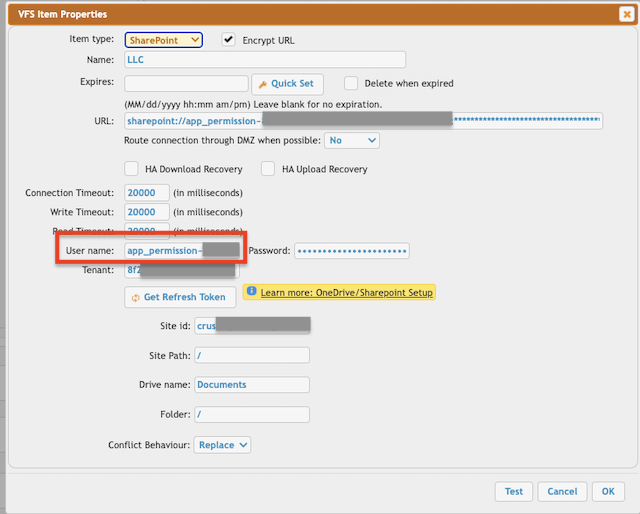
User name: Itt must start with "app_permission", then the Client ID separated with tilda.
app_permission~<<Client ID>>
Password: Client Secret.
Tennant: The tenant id. Tenant: See your App registration -> Overview -> EndPoints. Based on the App Registration Account type it can be an ID, common, or consumer.
Provide the SharePoint-specific settings. See under the 1.3.Sharepoint-specific settings. ( Link: https://www.crushftp.com/crush10wiki/Wiki.jsp?page=SharePoint%20Integration#section-SharePoint+Integration-1.3.SharepointSpecificSettings

1.2 Delegated Permission:
#
Client id : You can find it at Azure portal -> App Registration -> Overview:

Secret key: A new client secret needs to be created as well. Go to the "Certificate & secrets" and generate a new secret key. Click on New client secret.


SharePoint remote item settings:
!!! The CrushFTP admin page URL must match the redirect URL. In our example : http://localhost:9090
Select the SharePoint item type and click on the "Get Refresh Token" button. Provide the Client ID and Client Secret Value (not ID, see the screenshot), and Tenant (in almost all cases it is just: common).
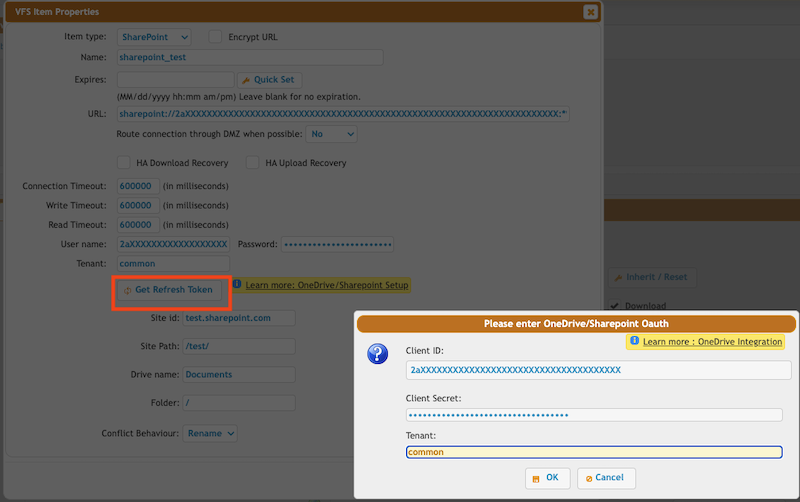
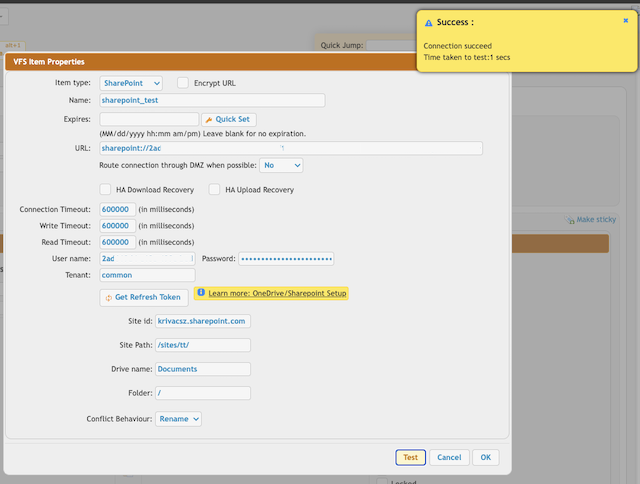
Click on the "OK" button, log in with your Azure credentials, and allow CrushFTP to have access to your SharePoint files. After that the form will disappear and the username and password will be filled. Done.
1.3.Sharepoint-specific settings:
#
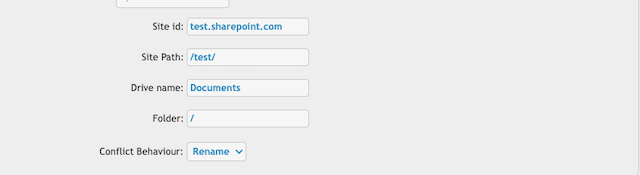
_Site id : The SharePoint domain name.
Site Path: The path of the SharePoint site. It should start and end with a slash.
Drive name: Each SharePoint site has a document library where the site-related files are stored. See https://support.microsoft.com/en-us/office/what-is-a-document-library-3b5976dd-65cf-4c9e-bf5a-713c10ca2872
 Provide its name.
Provide its name.Folder: Relative path of the document library of the SharePoint site.
Conflict Behaviour:
- Rename the file/folder if already exits
- Replace the file/folder if already exits
- Fail if the file/folder already exists
2. SharePoint REST service API-based integration
#
Remote item name: Sharepoint2More info : https://docs.microsoft.com/en-us/sharepoint/dev/sp-add-ins/get-to-know-the-sharepoint-rest-service?tabs=csom

!!!Constraint: On newer Sharepoint (after 2019) Grant App permission as it is disabled by default. To enable Custom Application APP Authentication run the following PowerShell commands:
Install-Module -Name Microsoft.Online.SharePoint.PowerShell $adminUPN="<SharePoint administrator account>" $orgName="<name of your Office 365 organization>" $userCredential = Get-Credential -UserName $adminUPN -Message "Type the password." Connect-SPOService -Url https://$orgName-admin.sharepoint.com -Credential $userCredential get-spotenant | Select DisableCustomAppAuthentication set-spotenant -DisableCustomAppAuthentication $false
Or
$creds = Get-Credential $orgName="<name of your Office 365 organization>" Connect-SPOService -Url https://$orgName-admin.sharepoint.com -Credential $creds get-spotenant | Select DisableCustomAppAuthentication set-spotenant -DisableCustomAppAuthentication $false
Advantage(Compared with MSGraph API Delegated Permission): Stream upload supported. There is no temporarily stored local file during the upload.
1. Register Add-In
Navigate and log in to the SharePoint online site. Got to the Register Add-In page by entering the URL as:
https://<sitename>.sharepoint.com/<<site path>>/_layouts/15/appregnew.aspx
Click the Generate button.
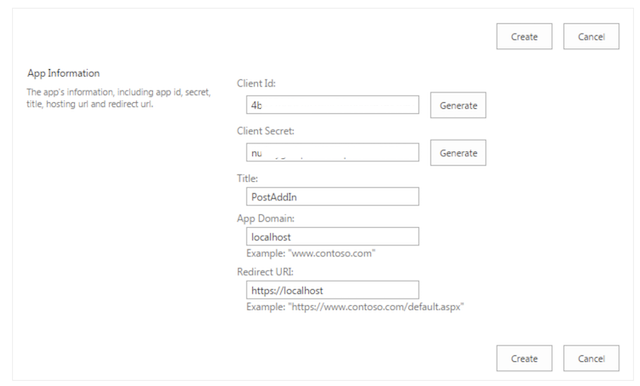
Store the Client ID and Client Secret and click on Create button.
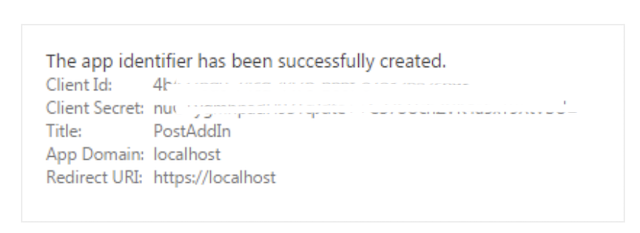
2. Grant Permissions to Add-In
Navigate to:
https://<sitename>.sharepoint.com/<<site path>>/_layouts/15/appinv.aspx
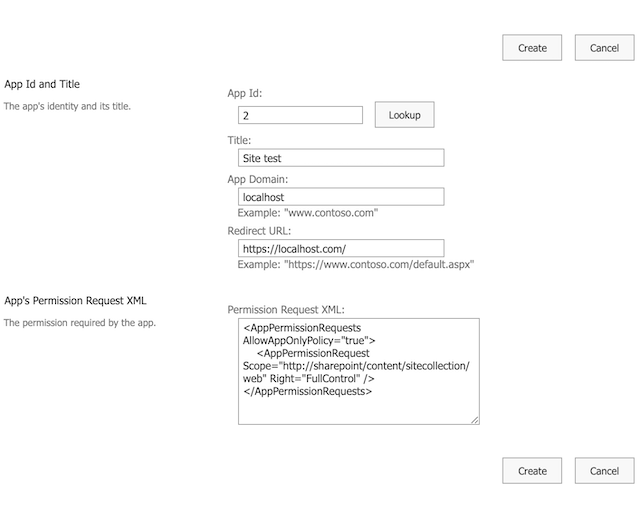
This will redirect to the Grant permission page. Enter the Client ID(generated earlier), in the AppId textbox and click the Lookup button.
Provide the permission Request xml and click on Create button.
Permission Request XML content:
<AppPermissionRequests AllowAppOnlyPolicy="true"> <AppPermissionRequest Scope="http://sharepoint/content/sitecollection/web" Right="FullControl"/></AppPermissionRequests>
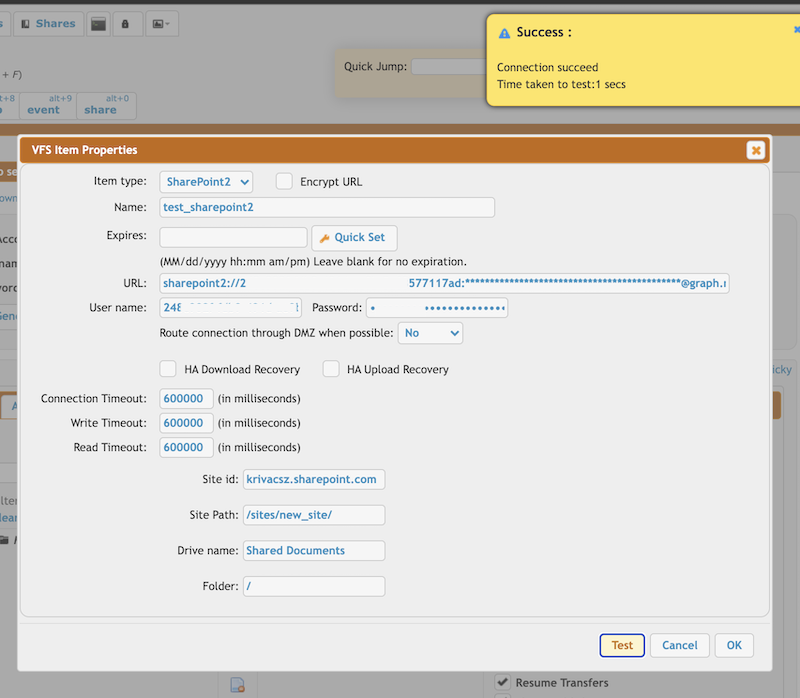
SharePoint2 remote item settings:
User name : The created Client ID
Password : The created Client Secret
Site id : The sharepoint domain name.
Site Path: The path of the SharePoint site. It should start and end with a slash.
Drive name: Each SharePoint site has a document library where the site-related files are stored. See https://support.microsoft.com/en-us/office/what-is-a-document-library-3b5976dd-65cf-4c9e-bf5a-713c10ca2872
 Provide its name
Provide its nameFolder: Relative path of the document library of the sharepoint site.
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
app_inv_permission.png | 64.3 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
app_permission_admin_consent.p... | 85.3 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
app_permission_vfs_item.png | 111.7 kB | 3 | 01-May-2025 02:48 | krivacsz | |
png |
app_reg_new.png | 57.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
app_reg_new_success.png | 58.7 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
client_id.png | 93.9 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
ms_graph_app_permission.png | 85.0 kB | 1 | 01-May-2025 02:20 | krivacsz | |
png |
new_registration.png | 83.3 kB | 3 | 05-Dec-2023 05:32 | krivacsz | |
png |
new_secret.png | 81.9 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
permission_final.png | 165.2 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
permission_microsoft_graph.png | 182.9 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
register_app.png | 230.6 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
remote_item_done.png | 92.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
remote_item_settings.png | 107.4 kB | 2 | 01-May-2025 05:18 | krivacsz | |
png |
remote_item_sharepoint_specifi... | 22.8 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
secret_value.png | 88.6 kB | 2 | 03-May-2025 02:37 | krivacsz | |
png |
sharepoint2_refresh_token_vfs_... | 203.1 kB | 1 | 01-May-2025 15:04 | krivacsz | |
png |
sharepoint2_vfs.png | 165.8 kB | 1 | 05-Dec-2023 05:32 | krivacsz |
«
This particular version was published on 01-May-2025 02:09 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki