A RFC compliant pure SFTP/SCP server implementation. SSH Tunneling is supported in CrushFTP. An SSH shell is not allowed as its often the method used in exploits. A shell has no purpose in file transfer.
compliant pure SFTP/SCP server implementation. SSH Tunneling is supported in CrushFTP. An SSH shell is not allowed as its often the method used in exploits. A shell has no purpose in file transfer.
Public / Private key authentication is supported too. The ciphers can be customized to prevent wasted CPU usage from inefficient ciphers.
By default, there is an SFTP server listener configured with compatible defaults bound to port 2222 readily available on first deploy.
For a little more control, we let you control outbound SFTP connections and limit the possible options via prefs.XML file. Edit it manually to set these:
 compliant pure SFTP/SCP server implementation. SSH Tunneling is supported in CrushFTP. An SSH shell is not allowed as its often the method used in exploits. A shell has no purpose in file transfer.
compliant pure SFTP/SCP server implementation. SSH Tunneling is supported in CrushFTP. An SSH shell is not allowed as its often the method used in exploits. A shell has no purpose in file transfer.Public / Private key authentication is supported too. The ciphers can be customized to prevent wasted CPU usage from inefficient ciphers.
By default, there is an SFTP server listener configured with compatible defaults bound to port 2222 readily available on first deploy.
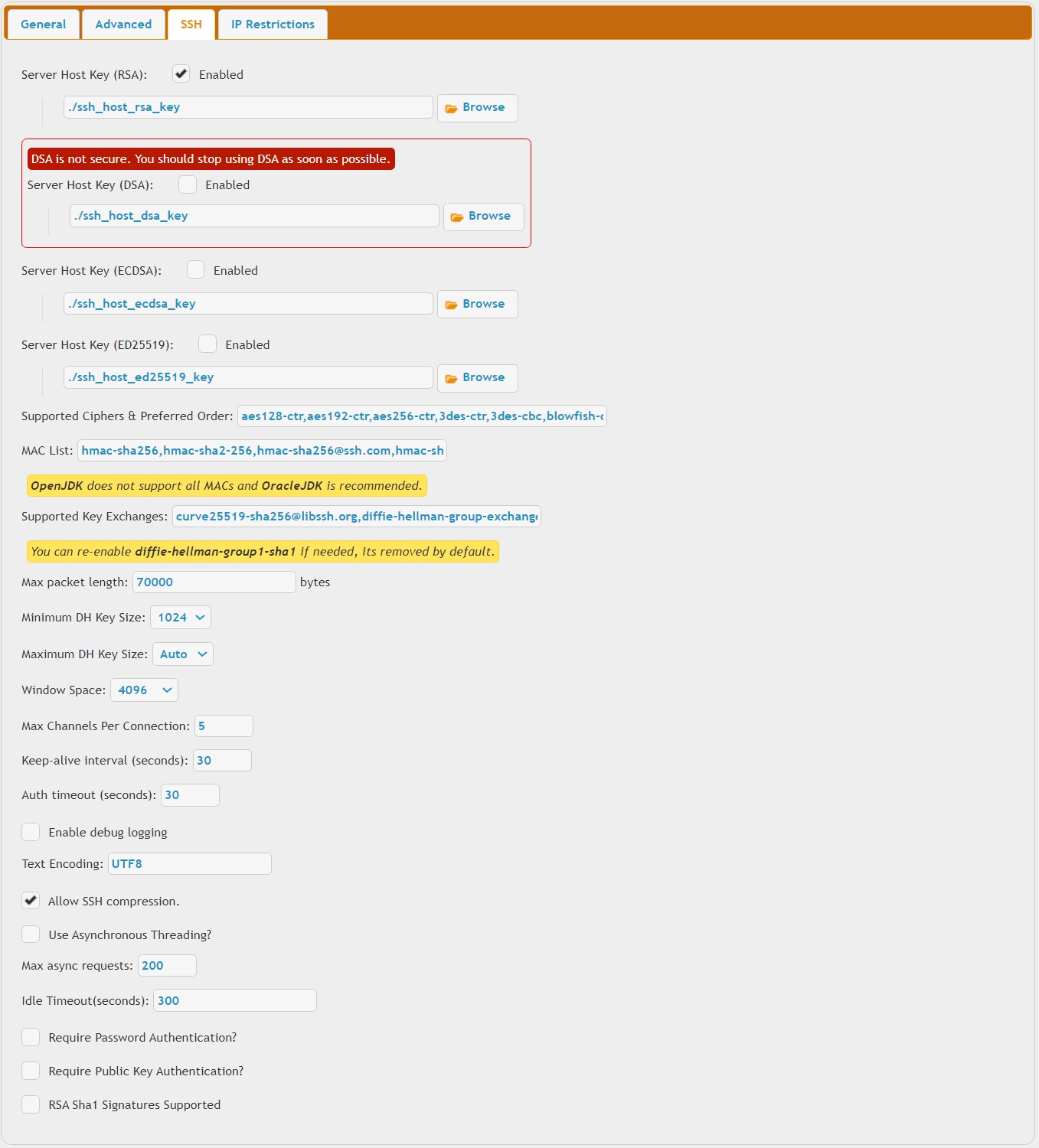 |
Supported ciphers:#
aes128-ctr,aes192-ctr,aes256-ctr,3des-ctr,3des-cbc,blowfish-cbc,arcfour,arcfour128,arcfour256,aes128-gcm@openssh.com,aes256-gcm@openssh.comaes128-cbc,aes192-cbc,aes256-cbc,chacha20-poly1305@openssh.com are also supported but not recommended due to their known insecurity.
Supported KEX:#
curve25519-sha2@libssh.org,curve25519-sha256@libssh.org,diffie-hellman-group-exchange-sha256,diffie-hellman-group18-sha512,diffie-hellman-group17-sha512,diffie-hellman-group16-sha512,diffie-hellman-group15-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha1diffie-hellman-group1-sha1 is also supported but it is not considered secure.
Supported MACs:#
hmac-sha256,hmac-sha2-256,hmac-sha256@ssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-256-96,hmac-sha512,hmac-sha2-512,hmac-sha512@ssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2-512-96,hmac-sha1,hmac-sha1-etm@openssh.com,hmac-sha1-96,hmac-ripemd160,hmac-ripemd160@openssh.com,hmac-ripemd160-etm@openssh.com,hmac-md5,hmac-md5-etm@openssh.com,hmac-md5-96
For a little more control, we let you control outbound SFTP connections and limit the possible options via prefs.XML file. Edit it manually to set these:
ssh_client_key_exchanges ssh_client_cipher_list ssh_client_mac_list
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
sftp_ssh.png | 71.2 kB | 2 | 05-Dec-2023 05:32 | Sandor | new ECDSA and ED25519 hosts |
jpg |
sftp_ssh2.jpg | 307.9 kB | 1 | 09-Apr-2024 12:50 | Ada Csaba | |
png |
ssh.png | 69.6 kB | 2 | 05-Dec-2023 05:32 | Ben Spink |
«
This page (revision-23) was last changed on 04-Nov-2025 02:27 by Ben Spink
G’day (anonymous guest)
Log in
JSPWiki