Amazon supports custom SAML 2.0 applications. See Amazon: Set up your own SAML 2.0 application Link

⚠️ Important: Redirect of CrushFTP user to the SAML provider is not supported.
https://domain.com/?u=SSO_SAML&p=redirect
1. Amazon SSO SAML 2.0 Configurations:#
Open the IAM Identity Center Console Link
 and create a new custom application.
and create a new custom application.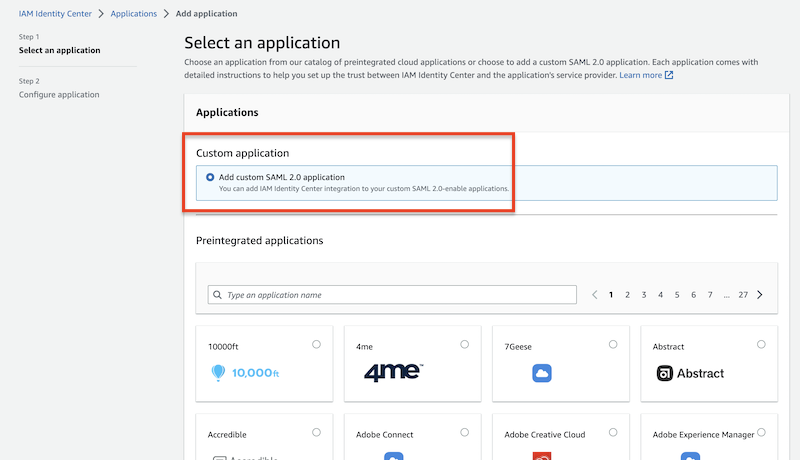
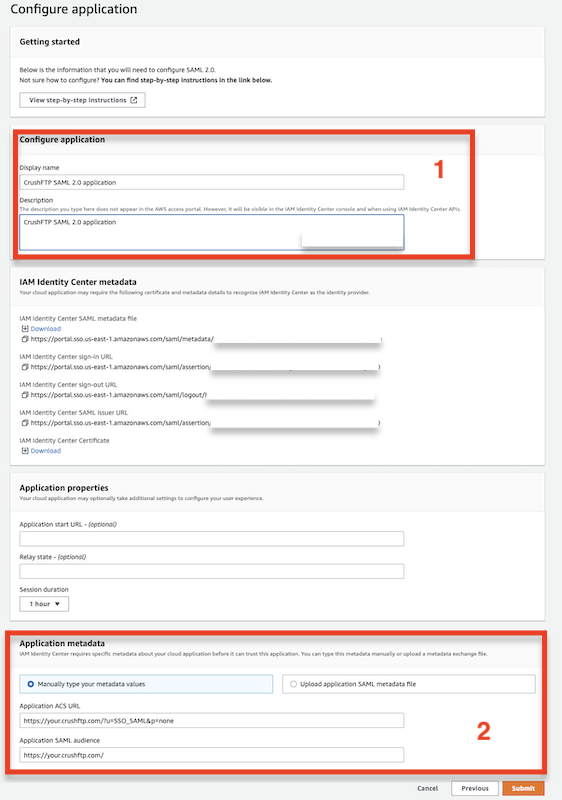
Configure SAML Settings:
Enter the Application Name, Application ACS URL, and SAML Audience in the provided fields.
Once all required values are set, click Submit to complete the application setup.
Application ACS URL example: https://your.crushftp.com/?u=SSO_SAML&p=none
SAML Audience example: https://your.crushftp.com/
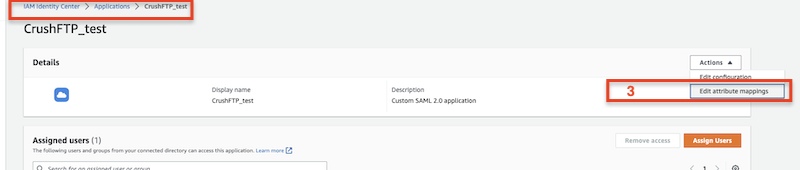
Configure Attribute Mappings:
Set up the attribute mappings for your application to define which user details (such as username, email, or roles) are passed during the SAML authentication process.
These mappings ensure that the correct user information is shared between your identity provider and the application.
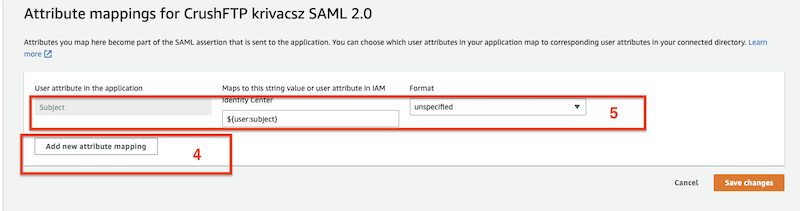
Add New Attribute Mapping:
To create a new attribute mapping, specify the value you want to send to the application. In the field Maps to this string value or user attribute in IAM Identity Center, enter:
Maps to this string value or user attribute in IAM Identity Center:
${user:subject}
This maps the attribute to the user’s unique identifier in IAM Identity Center, typically used as the username or user ID during authentication.
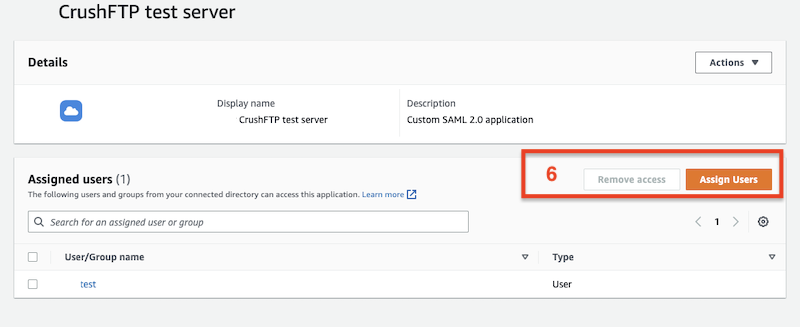
⚠️ Warning: Assign Users/Groups to the Application!
After creating the application, make sure to assign the appropriate users or groups to it in your IAM Identity Center.
2. SAMLSSO plugin configuration
#
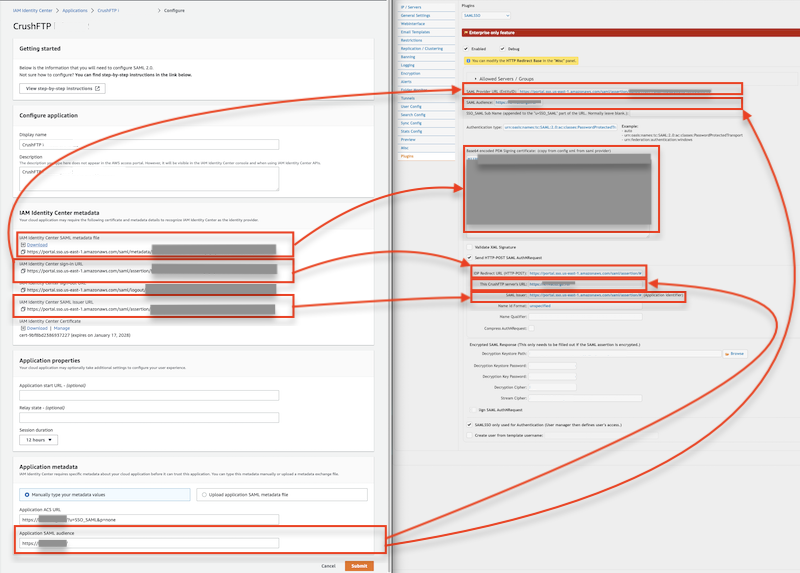
⚠️ Download the IAM Identity Center SAML metadata file. This file contains important configuration details required by the service provider (e.g., CrushFTP) to establish a secure SAML connection.
[Amazon SSO SAML 2.0 Configuration] [CrushFTP settings] entityID value of IAM Identity Center SAML metadata XML file -> SAML Provider URL (EntityID) Application SAML audience -> SAML Audience SingleSignOnService SAML:2.0:bindings:HTTP-POST Location value of IAM Identity Center SAML metadata XML file -> IDP Redirect URL (HTTP-POST) IAM Identity Center SAML issuer URL -> SAML Issuer X509Certificate value of IAM Identity Center SAML metadata XML file -> Base64 encoded PEM Signing certificate
On CrushFTP SAMLSSO plugin for "Authentication type:" set "urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport".
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
csutom_app_new_attribute.png | 55.0 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
custom_app.png | 105.1 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
custom_app_assign_users.png | 64.1 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
custom_app_attribute_mappings_... | 43.2 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
custom_app_crushftp_settings.p... | 217.3 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
custom_app_settings.png | 149.6 kB | 1 | 05-Dec-2023 05:32 | krivacsz |
«
This particular version was published on 22-May-2025 05:03 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki