S3 Integration Overview:
#
⚠️ General restrictions: This integration allows you to use an Amazon S3 bucket as the backend virtual file system (VFS) in CrushFTP. However, since S3 is not a true hierarchical file system, folder structures are simulated using object key prefixes. These are not limitations imposed by CrushFTP, but inherent to S3’s object storage architecture, which is optimized for static content access, not for dynamic file manipulation.
⚠️ Proxy Configuration: If your server accesses the internet through a proxy, ensure that the necessary S3 domains are whitelisted to allow successful communication with the S3 REST API.
1. Amazon S3 Configuration.
#
The URL should be structured as follows (replace placeholders with your actual values):
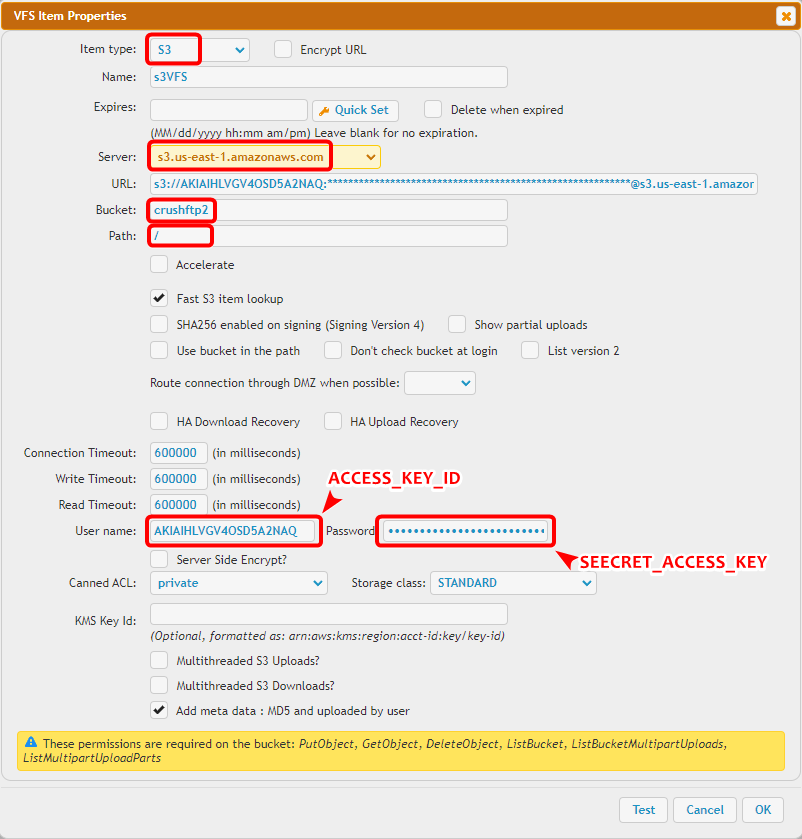
General S3 : s3://ACCESS_KEY_ID:SEECRET_ACCESS_KEY@SERVER/BUCKET/ Amazon S3 Example: s3://AKIAEXAMPLE:abcd1234example@s3.amazonaws.com/my-bucket/
1.1 Access Key Authentication
#
To authenticate using standard Amazon S3 credentials:
• Access Key ID – Your AWS access key.
• Secret Access Key – The corresponding secret key.
The Access Key ID and Secret Access Key are generated and offered for download when creating an S3 user (IAM user) in the AWS Management Console.
⚠️ Make sure to save them securely, as the secret key will not be shown again.
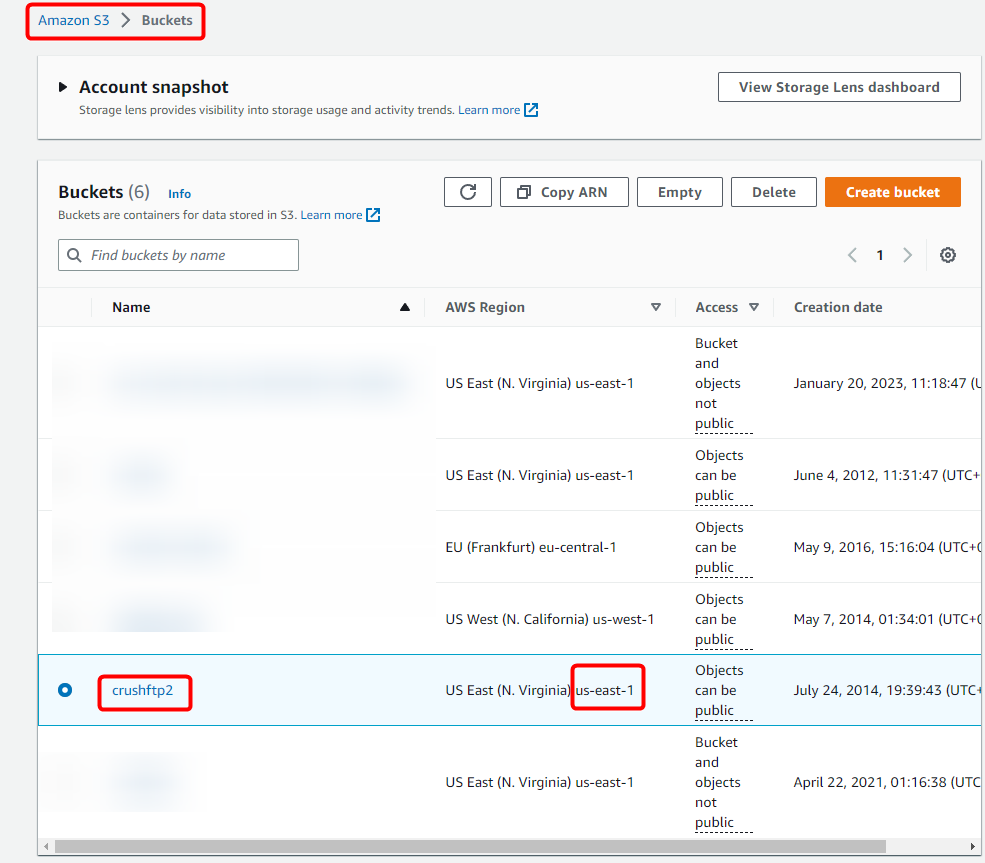
The S3 server endpoint and bucket name can be found in the AWS Console under: S3 -> Buckets. This information is required to correctly configure your S3 integration.
1.2 Amazon EC2 IAM Authentication Support
#
CrushFTP supports S3 authentication using IAM roles assigned to EC2 instances. This allows secure access without embedding static credentials.
To use this mode:
• Set the S3 Username to: iam_lookup
• Set the S3 Password to: lookup
This instructs CrushFTP to automatically retrieve temporary credentials from the EC2 instance’s IAM role via the instance metadata service. Use this approach to securely avoid hardcoding static credentials in environments where IAM roles are configured properly.
Then paste them on the appropriate fields in CrushFTP.
The following policy permissions are needed on S3:
"s3:GetBucketLocation", "s3:ListAllMyBuckets", "s3:ListBucket", "s3:ListBucketMultipartUploads", "s3:PutObject", "s3:AbortMultipartUpload", "s3:ListMultipartUploadParts", "s3:DeleteObject", "s3:GetObject", "s3:GetObjectAttributes"
2. Access other cloud storage through S3 REST API
#
Google Cloud - Google Cloud Storage Access Through S3 REST API

BackBlaze(b2) - BackBlaze(b2) Access Through S3 REST API

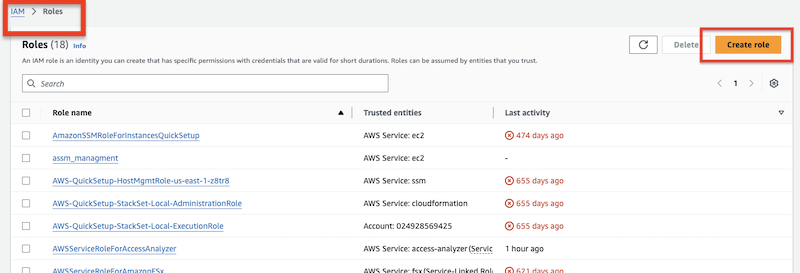
3. Assume Role access
#
You can use IAM roles to delegate access to your AWS resources. With IAM roles, you can establish trust relationships between your trusting account and other AWS trusted accounts. (for more info see: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-user.html
 , and https://docs.aws.amazon.com/STS/latest/APIReference/API_AssumeRole.html
, and https://docs.aws.amazon.com/STS/latest/APIReference/API_AssumeRole.html )
)Create the assume role at Identity and Access Management (IAM):
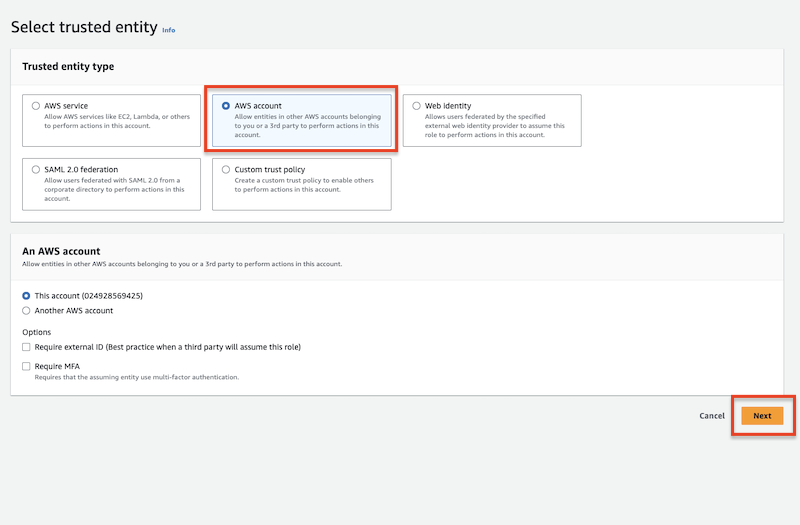
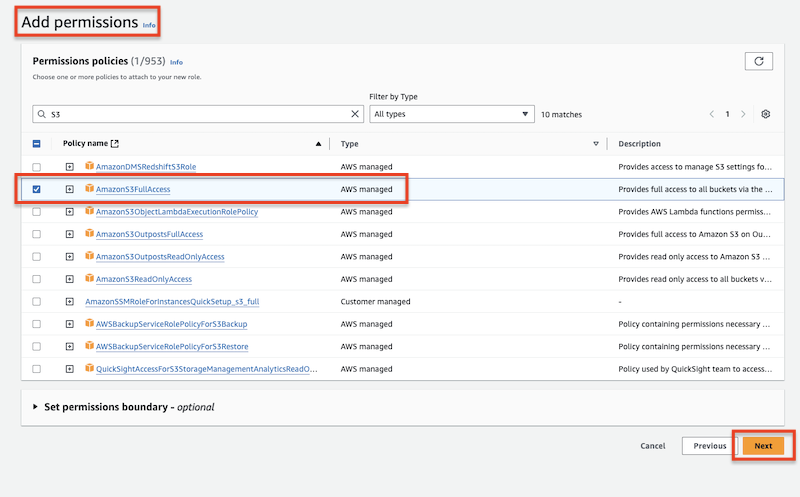
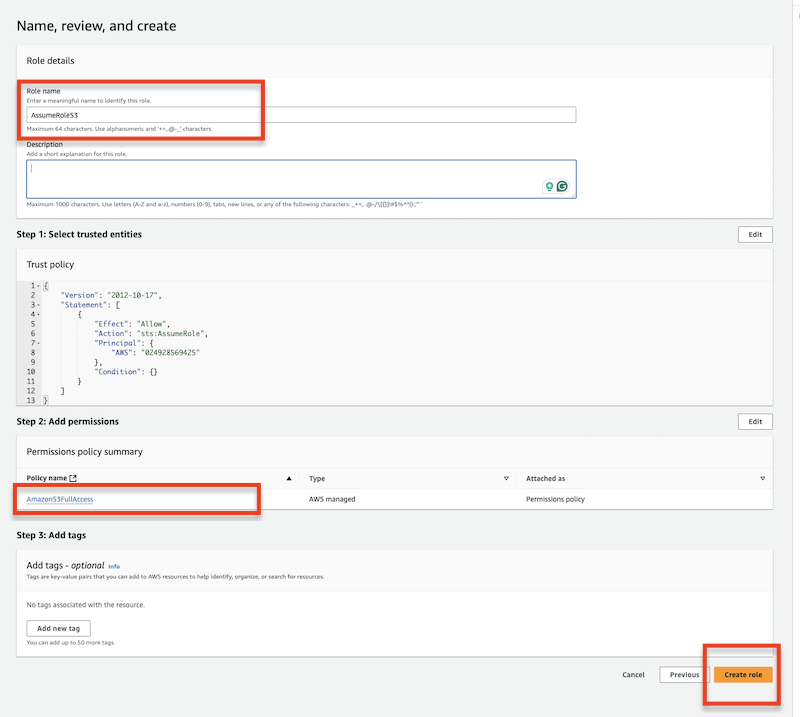
Add permission policy to the specified user. This policy will use the above-created assume role.
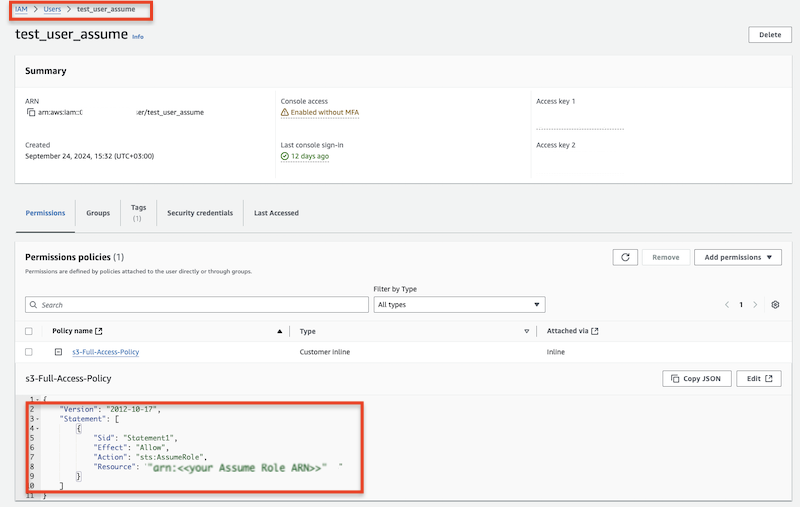
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::XXXXX:role/AssumeRoleS3"
}
]
}
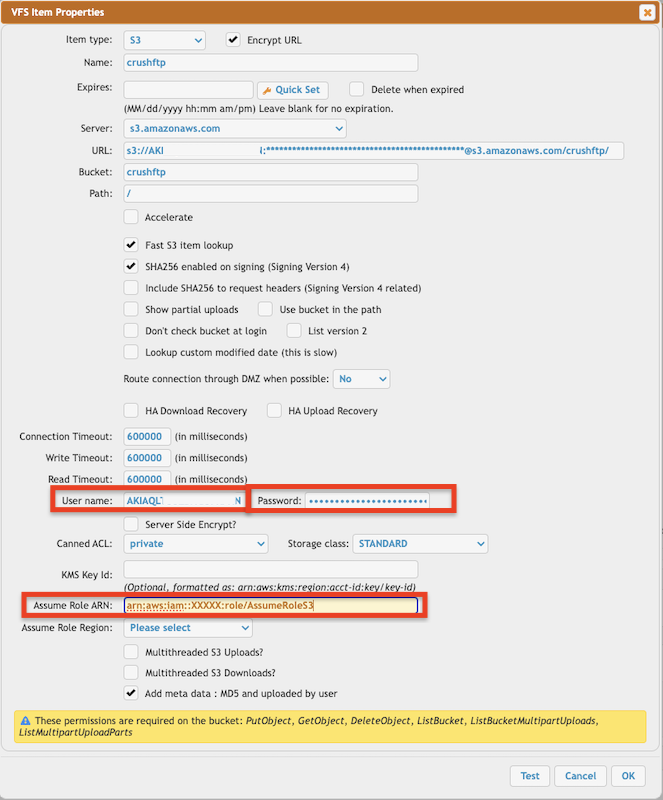
Use the specified user's Access key and Secret along with the Assume Role ARN to obtain S3 access.
Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
S3_VFS_config.png | 143.0 kB | 2 | 20-May-2025 04:42 | krivacsz | |
png |
S3_bucket_info.png | 99.3 kB | 1 | 05-Dec-2023 05:32 | Sandor | |
png |
assume_create_role_final_check... | 119.7 kB | 1 | 07-Oct-2024 07:25 | krivacsz | |
png |
assume_role_entity_type.png | 94.2 kB | 1 | 07-Oct-2024 07:16 | krivacsz | |
png |
assume_role_s3_access.png | 140.2 kB | 1 | 07-Oct-2024 07:20 | krivacsz | |
png |
assume_role_user_permission_po... | 103.9 kB | 1 | 07-Oct-2024 07:36 | krivacsz | |
png |
assume_role_vfs_settings.png | 183.7 kB | 2 | 07-Oct-2024 08:02 | krivacsz | |
png |
create_assume_role.png | 84.5 kB | 1 | 07-Oct-2024 07:14 | krivacsz | |
png |
s3_ec2_general_settings.png | 30.1 kB | 1 | 20-May-2025 03:50 | krivacsz |
«
This particular version was published on 20-May-2025 03:12 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki