Constraints: It requires Enterprise License.
#
OTP / MFA / 2FA settings:
This settings allows you to configure Two Factor authentication.
This feature also supports software-based authenticator applications such as Google Authenticator and Microsoft Authenticator. For more information, see the Authenticator Link
1. Ensure that “Validated Logins?” is enabled to allow two-factor authentication.
#
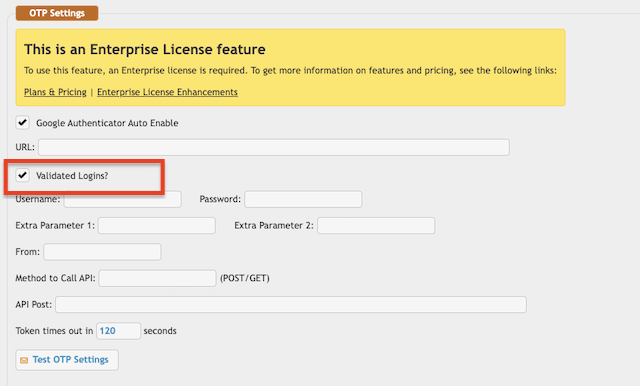
DMZ Links - Main node scenario: on Preferences -> General Settings -> OTP section the "Validated Logins" option must be enabled on the DMZ node, so the DMZ gives the two-factor authentication to the Main node.
2. SMS based:#
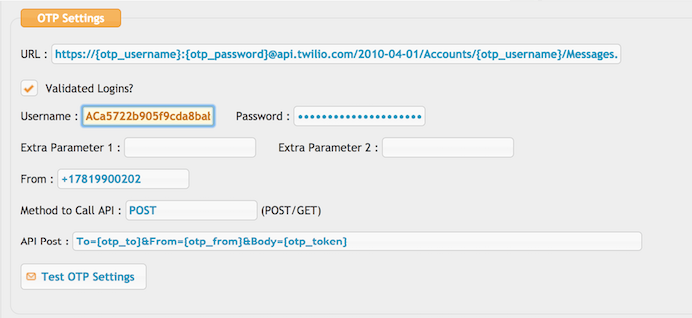
- You must have a twilio account.
Using Twilio: Twilio Link
!!! Proxy Configuration: If your server accesses the internet through a proxy, make sure to whitelist the following domain: api.twilio.com
The ACCOUNT SID as username and AUTH TOKEN as password:
URL :
https://{otp_username}:{otp_password}@api.twilio.com/2010-04-01/Accounts/{otp_username}/Messages.json
API post :
To={otp_to}&From={otp_from}&Body={otp_token}
Provide your twilio phone number.
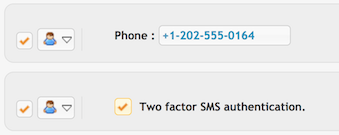
The config will be used only for users which have a phone number and the "Two factor SMS authentication" flag enabled in the User Manager.
3. Email based:#
Email usage requires an SMTP Server configured in the Preferences, General Settings area.
Url : SMTP
(Just those 4 uppercase letters, nothing else.)
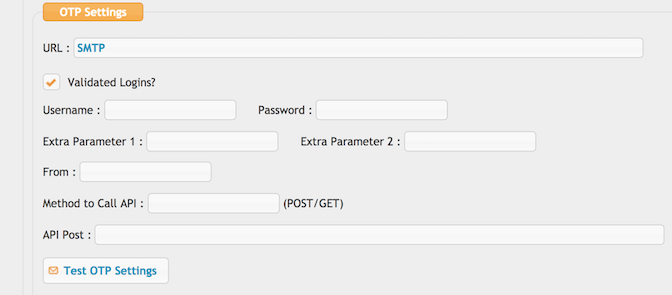
The configuration will apply only to users who have an email address and have the Two-factor OTP/SMS authentication flag enabled in the User Manager.
The email can be customized by creating an email template: Two Factor Auth
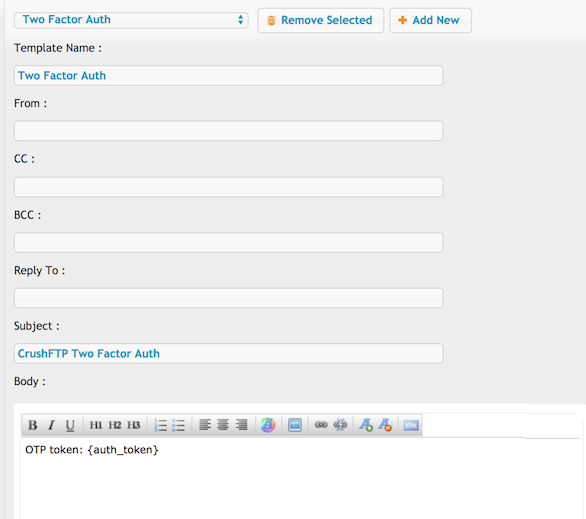
Variable for the one time password : {auth_token}
OTP's mainly for Webinterface logins, variants like Google Authenticator TOPT would be straight meaningless for FTP, SFTP, since it's impossible enroll anyways.
A hidden flag in prefs.XML controls for which protocols OTP should be enabled by default
<twofactor_secret_auto_otp_enable_protocols>ftp,ftps,sftp,http,https,webdav</twofactor_secret_auto_otp_enable_protocols>
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
otp_email.png | 53.8 kB | 2 | 05-Dec-2023 05:32 | Ben Spink | |
png |
otp_email_template.png | 66.4 kB | 2 | 05-Dec-2023 05:32 | Ben Spink | |
png |
otp_email_template2.png | 56.3 kB | 1 | 12-May-2025 04:52 | krivacsz | |
jpg |
otp_general.jpg | 166.9 kB | 1 | 05-Dec-2023 05:32 | Ada Csaba | |
png |
otp_sms.png | 89.8 kB | 2 | 05-Dec-2023 05:32 | Ben Spink | |
png |
otp_token_length_config.png | 58.9 kB | 1 | 23-May-2025 02:26 | krivacsz | |
png |
otp_user_extra_text_ref.png | 32.5 kB | 1 | 12-May-2025 04:49 | krivacsz | |
png |
otp_user_settings.png | 37.7 kB | 4 | 12-May-2025 05:34 | krivacsz | |
png |
otp_user_settings_phone.png | 15.7 kB | 1 | 12-May-2025 05:25 | krivacsz | |
png |
otp_validate_logins.png | 70.0 kB | 1 | 12-May-2025 04:12 | krivacsz | |
png |
twilio.png | 179.8 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
twilio2.png | 77.5 kB | 1 | 05-Dec-2023 05:32 | krivacsz | |
png |
twilio3.png | 24.1 kB | 2 | 05-Dec-2023 05:32 | Ben Spink |