Managing SharePoint Site Access for Applications Using Sites.Selected Permission
#
The Sites.Selected permission allows an app to access only the specific SharePoint sites you explicitly authorize. This wiki page provides guidance on how to grant SharePoint write access (required for SharePoint/SharePoint2 protocol see SharePoint Integration) to an App Registration configured in the Azure Portal. Using Sites.Selected offers a much more secure alternative to granting full access across your entire tenant. See this: https://learn.microsoft.com/en-us/sharepoint/dev/solution-guidance/security-apponly-azuread

1. Create an App Registration with permission Sites.FullControl.All
#
!!! Important: This App Registration is not the working app that will access the SharePoint site. It is a helper/admin app, used only to configure and grant SharePoint write permissions to other apps (the real apps that will use Sites.Selected permission).
Start at the Microsoft Azure portal: https://azure.microsoft.com/en-us/features/azure-portal/

Application registration: Go to the App registrations and click on New registration:
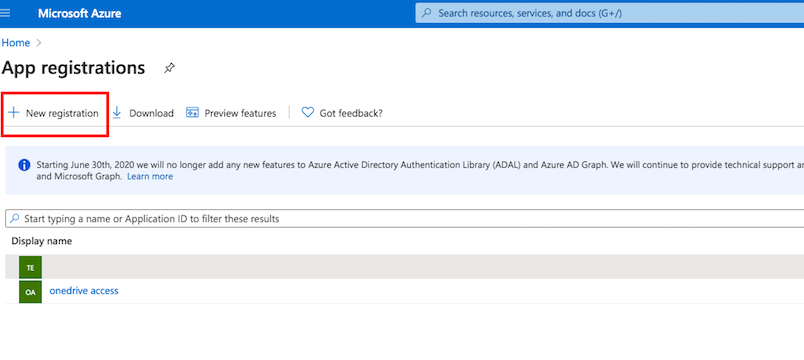
The Redirect URI (optional) is not required, because it will has a Application Permission only.
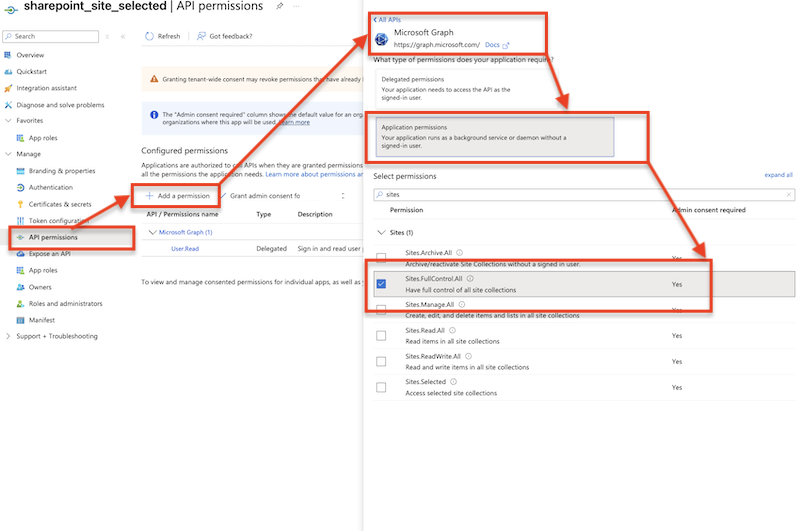
Configure API Permissions:
Navigate to API Permissions. Click on Add a permission button. Select Microsoft Graph. Then select Application Permission. Search for Sites and check the flag Sites.FullControll.All.
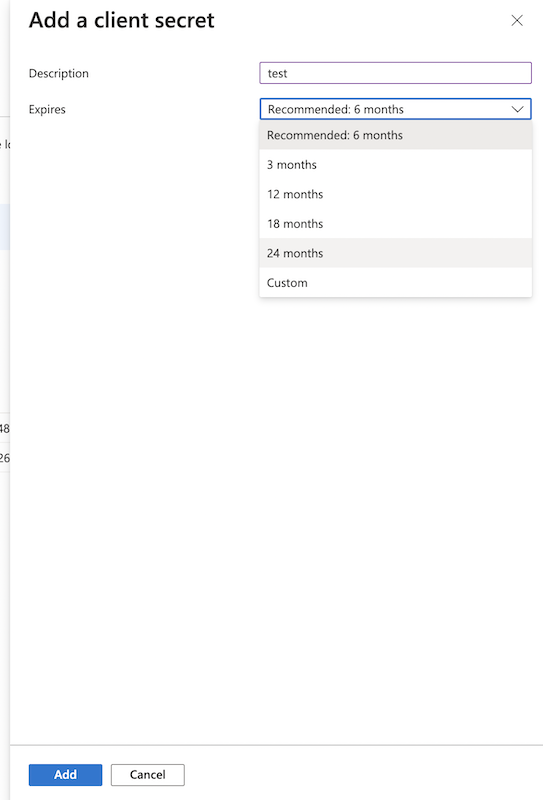
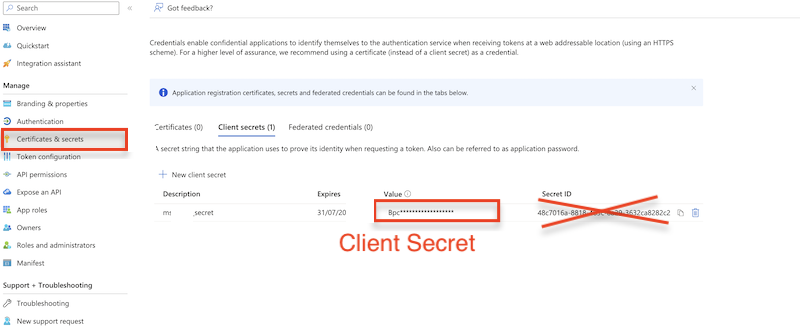
Secret key: A new client secret must be created. Go to Certificates & secrets, and generate a new client secret by clicking on New client secret. Ensure you copy over the value immediately!
2. Create an App Registration to Access Specific SharePoint Site Documents Using the Sites.Selected Permission
#
Application registration: Go to the App registrations and click on New registration. Select platform: Web and Configure redirect URL like:
http://localhost:9090/register_microsoft_graph_api/
or
https://your.crushftp.domain.com/register_microsoft_graph_api/
Navigate to API Permissions. Click on Add a permission button. Select SharePoint or Microsoft Graph. Then select Delegated/Application Permission. Search for Sites and check the flag Sites.Selected.
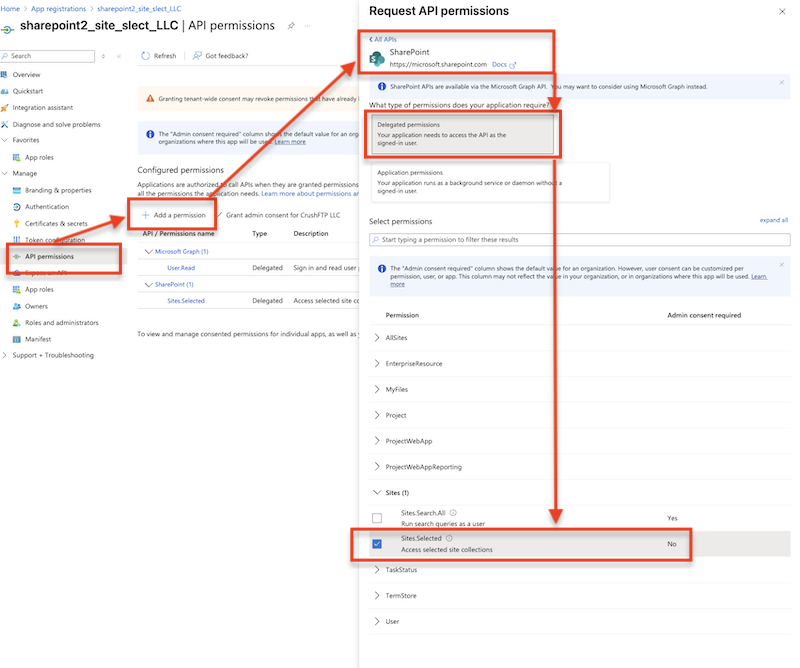
App Permissions for SharePoint REST API (See at: https://learn.microsoft.com/en-us/sharepoint/dev/sp-add-ins/get-to-know-the-sharepoint-rest-service?tabs=csom
 ):
):
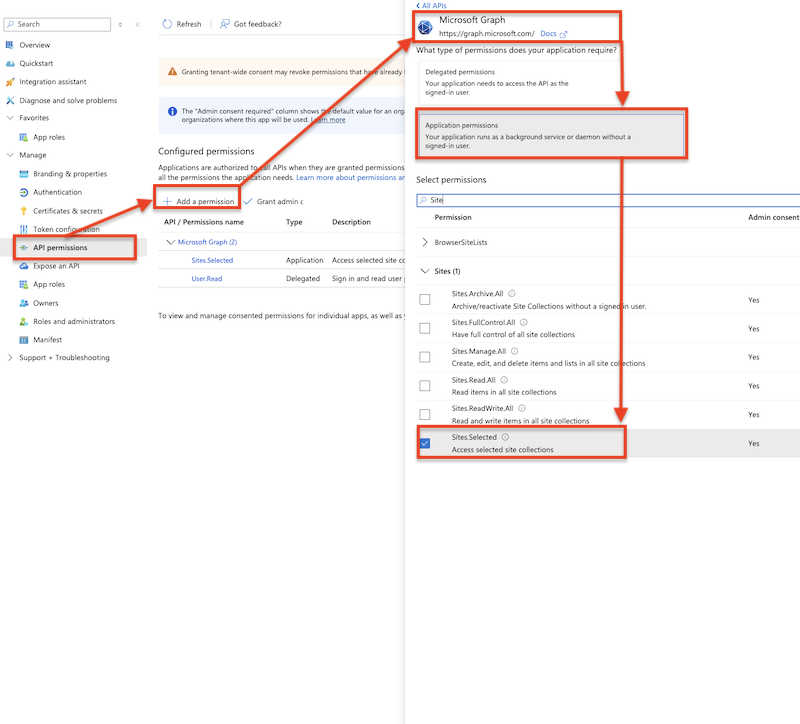
App Permissions for Microsoft Graph API (See at: https://learn.microsoft.com/en-us/sharepoint/dev/apis/sharepoint-rest-graph
 ):
):
Secret key: A new client secret must be created. Go to Certificates & secrets, and generate a new client secret by clicking on New client secret. Ensure you copy over the value immediately!
3. How to Grant SharePoint Site Access to an App Registration Using the Microsoft Graph API?
#
This is done by calling the /permissions endpoint on the target SharePoint site. The request must include a valid Microsoft Graph access token with Sites.FullControl.All application permission, and specify the App Registration you want to grant access to using the application.id in the request body:
POST https://graph.microsoft.com/v1.0/sites/{tenant}.sharepoint.com:/sites/{site-name}:/permissions
BODY: {
"roles": ["write"],
"grantedToIdentities": [
{
"application": {
"id": "11111111-2222-3333-4444-555555555555",
"displayName": "My Azure App Registration"
}
}
]
}
Curl example:
curl -X POST "https://login.microsoftonline.com/<<App Registration: Directory (tenant) ID>>/oauth2/v2.0/token" \ -H "Content-Type: application/x-www-form-urlencoded" \ -d "client_id=XXX-XXXX-XXX-XX&scope=https%3A%2F%2Fgraph.microsoft.com%2F.default&client_secret=XXX-XXXX-XXX-XX&grant_type=client_credentials"
curl -X POST "https://graph.microsoft.com/v1.0/sites/contoso.sharepoint.com:/sites/Your_Site:/permissions" \
-H "Authorization: Bearer YOUR_ACCESS_TOKEN" \
-H "Content-Type: application/json" \
-d '{
"roles": ["write"],
"grantedToIdentities": [
{
"application": {
"id": "11111111-2222-3333-4444-555555555555",
"displayName": "My Azure App Registration"
}
}
]
}'
PowerShell example:
$tenantId = "<<your-tenant-id>>" # Directory (tenant) ID
$clientId = "XXX-XXXX-XXX-XX" # App Registration (client ID)
$clientSecret = "XXX-XXXX-XXX-XX" # Client secret
$tokenEndpoint = "https://login.microsoftonline.com/$tenantId/oauth2/v2.0/token"
$body = @{
client_id = $clientId
scope = "https://graph.microsoft.com/.default"
client_secret = $clientSecret
grant_type = "client_credentials"
}
$response = Invoke-RestMethod -Method POST -Uri $tokenEndpoint -Body $body -ContentType "application/x-www-form-urlencoded"
# Output access token
$accessToken = $response.access_token
Write-Host "Access Token:" $accessToken
$accessToken = "YOUR_ACCESS_TOKEN"
$sitePath = "contoso.sharepoint.com:/sites/Your_Site:"
$uri = "https://graph.microsoft.com/v1.0/sites/$sitePath/permissions"
$headers = @{
"Authorization" = "Bearer $accessToken"
"Content-Type" = "application/json"
}
$body = @{
roles = @("write")
grantedToIdentities = @(
@{
application = @{
id = "11111111-2222-3333-4444-555555555555"
displayName = "My Azure App Registration"
}
}
)
} | ConvertTo-Json -Depth 5
Invoke-RestMethod -Method POST -Uri $uri -Headers $headers -Body $body
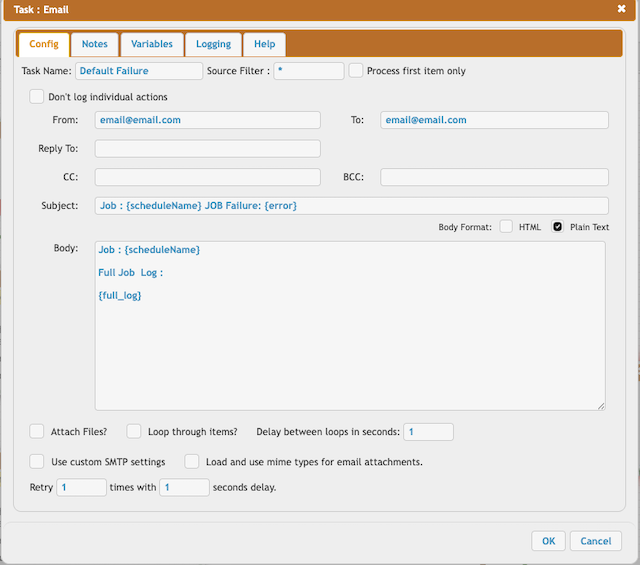
4. Job Example:
#
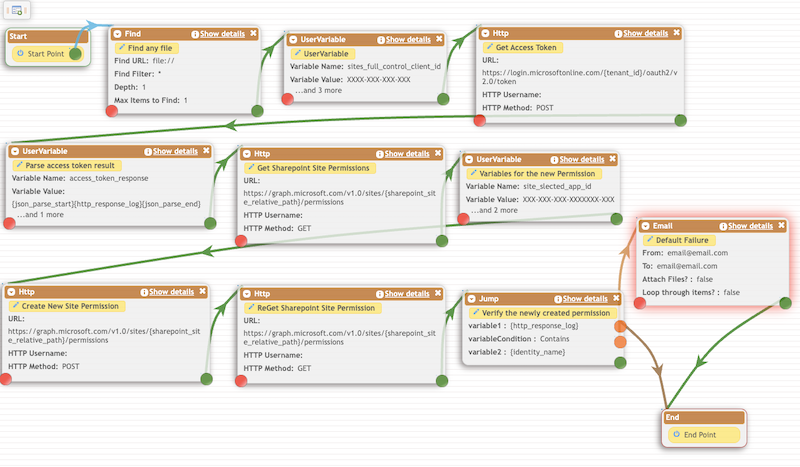
Tasks:
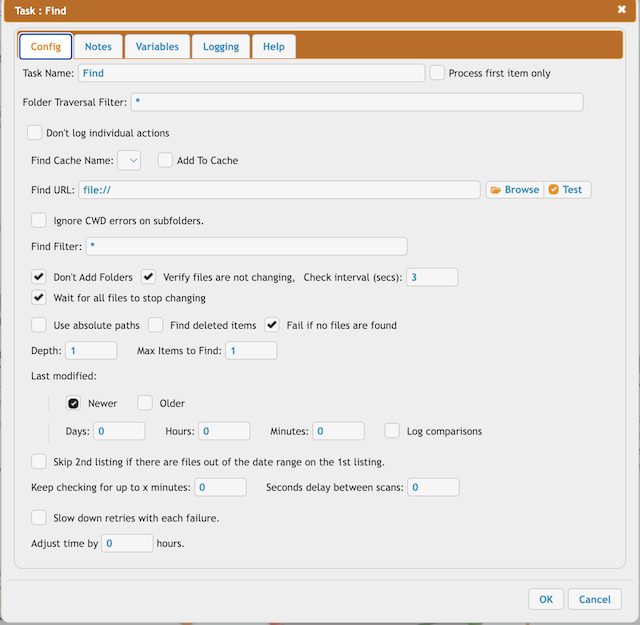
Find any local file on the server. Settings:
Don't Add Folders: true Max Items to Find: 1 Depth: 1
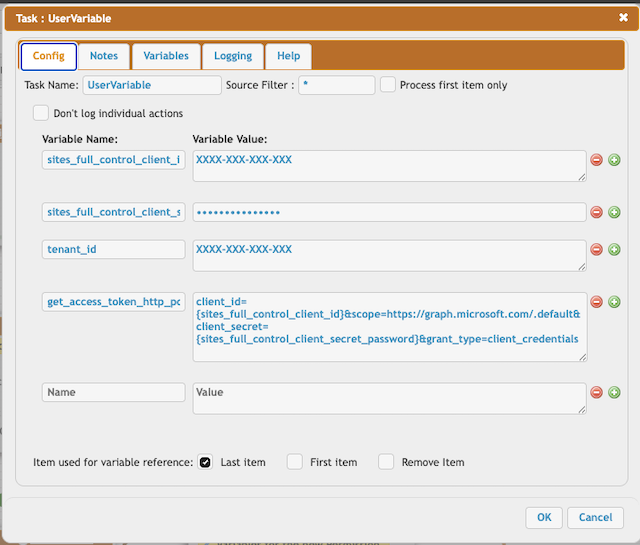
You need the following variables to obtain an access token:
sites_full_control_client_id = XXXX-XXX-XXX-XXX
(See at App Registration -> Overview -> Application (client) ID)
sites_full_control_client_secret_password = XXXX-XXX-XXX-XXX
(See at App Registration -> Manage -> Certificates & secrets)
tenant_id = XXXX-XXX-XXX-XXX
(See at App Registration -> Overview -> Directory (tenant) ID)
get_access_token_http_post_data = client_id={sites_full_control_client_id}&scope=https%3A%2F%2Fgraph.microsoft.com%2F.default&client_secret={sites_full_control_client_secret_password}&grant_type=client_credentials
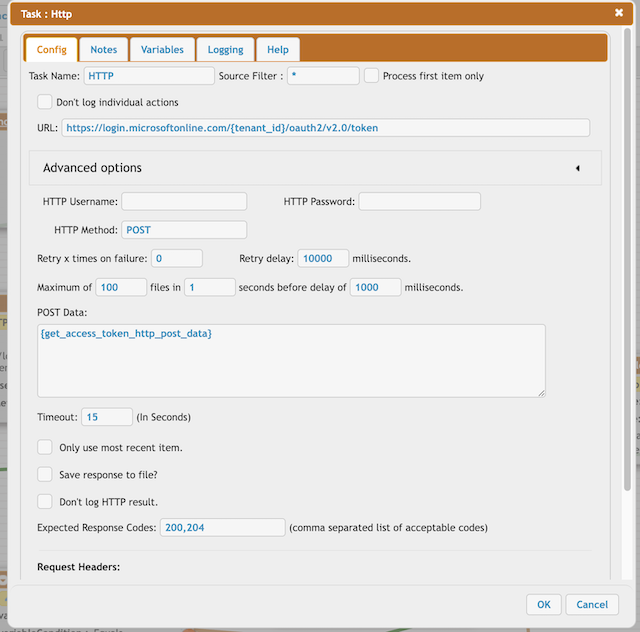
URL : https://login.microsoftonline.com/{tenant_id}/oauth2/v2.0/token
HTTP Method: POST
POST Data: {get_access_token_http_post_data}
Expected Response Codes: 200,204
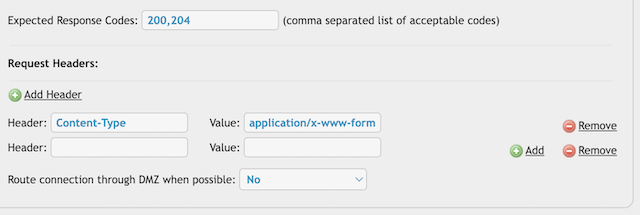
Header: Content-Type application/x-www-form-urlencoded
}}}
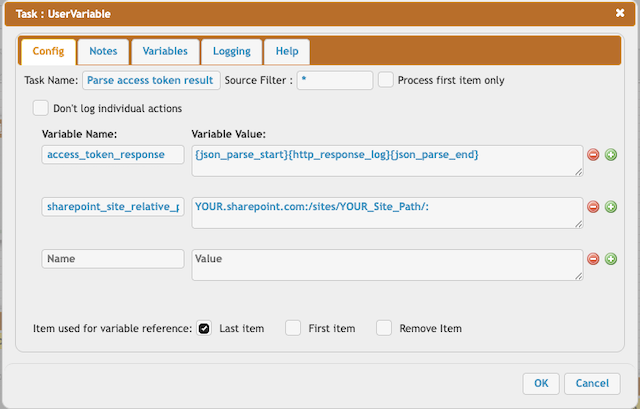
access_token_response = {json_parse_start}{http_response_log}{json_parse_end}
sharepoint_site_relative_path = YOUR.sharepoint.com:/sites/YOUR_Site_Path/:
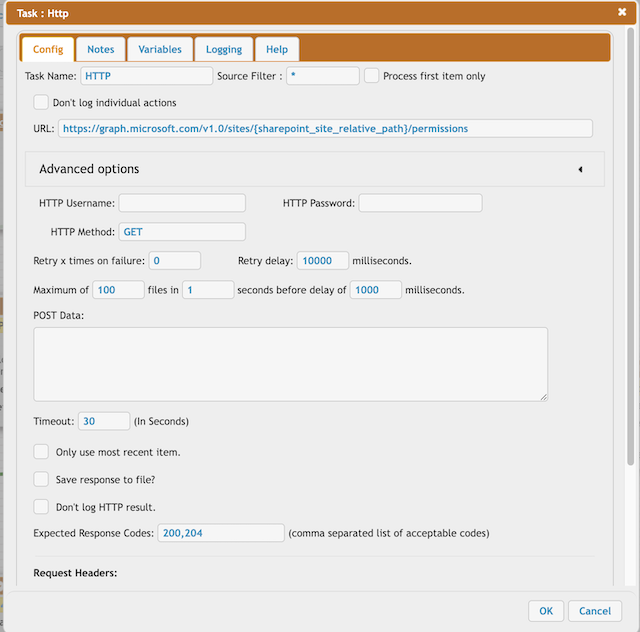
URL: https://graph.microsoft.com/v1.0/sites/{sharepoint_site_relative_path}/permissions
HTTP Method: GET
Expected Response Codes: 200,204
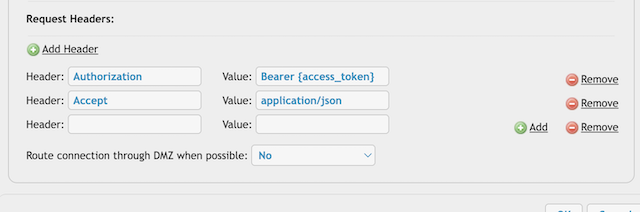
Header: Authorization Bearer {access_token}
Header: Accept application/json
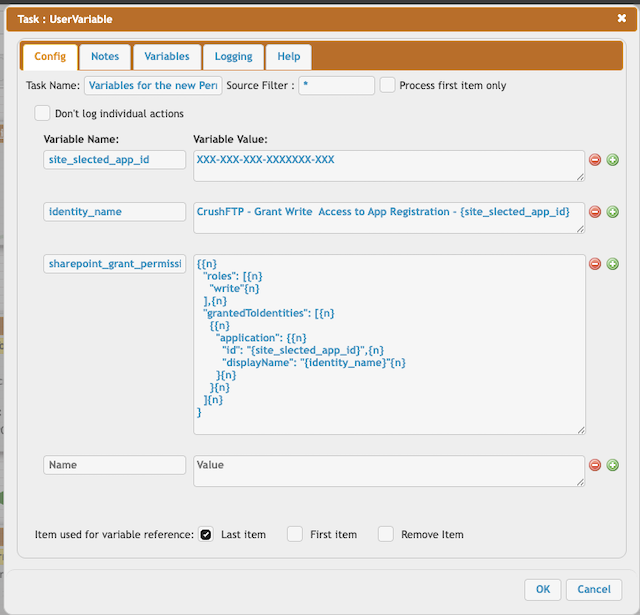
site_slected_app_id = XXXX-XXX-XXX-XXX
(See at App Registration -> Overview -> Application (client) ID)
identity_name = CrushFTP - Grant Write Access to App Registration - {site_slected_app_id}
sharepoint_grant_permission_http_post_data = {n}
"roles": [{n}
"write"{n}
],{n}
"grantedToIdentities": [{n}
{{n}
"application": {{n}
"id": "{site_slected_app_id}",{n}
"displayName": "{identity_name}"{n}
}{n}
}{n}
]{n}
}
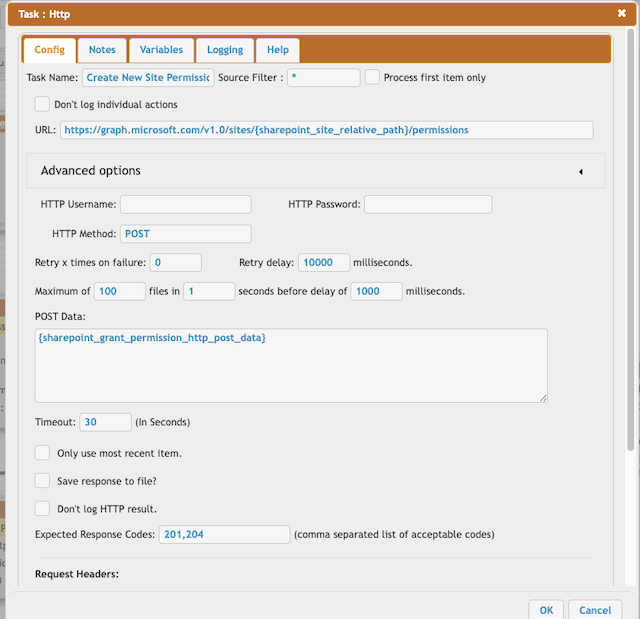
URL : https://graph.microsoft.com/v1.0/sites/{sharepoint_site_relative_path}/permissions
HTTP Method: POST
POST Data: {sharepoint_grant_permission_http_post_data}
Expected Response Codes: 201,204
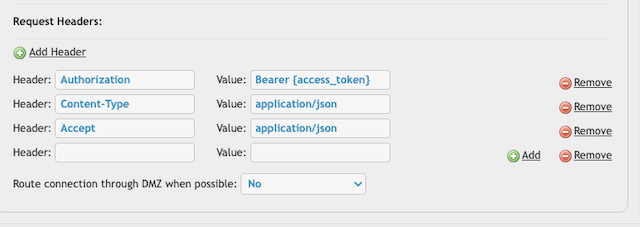
Header: Authorization Bearer {access_token}
Header: Content-Type application/json
Header: Accept application/json
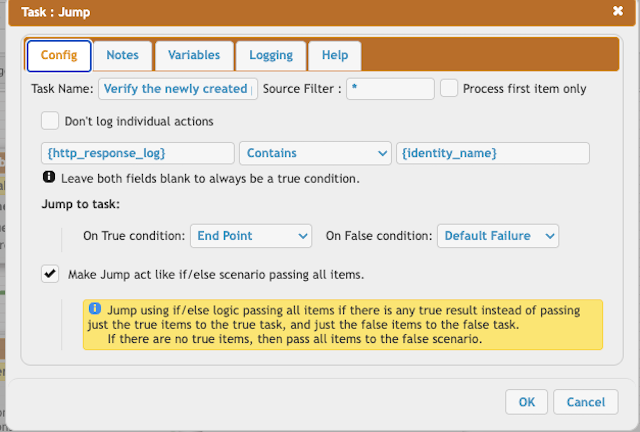
Reload the site permissions, including the newly created one.

Add new attachment
Only authorized users are allowed to upload new attachments.
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
app_permission_sharepoint_site... | 198.2 kB | 1 | 29-Apr-2025 11:24 | krivacsz | |
png |
app_permission_sites_full_cont... | 159.9 kB | 1 | 29-Apr-2025 09:55 | krivacsz | |
png |
check_new_permission.png | 112.3 kB | 1 | 30-Apr-2025 07:45 | krivacsz | |
png |
check_response_code.png | 118.7 kB | 1 | 29-Apr-2025 16:31 | krivacsz | |
png |
error_handler_task.png | 91.2 kB | 1 | 30-Apr-2025 07:44 | krivacsz | |
png |
find_a_file.png | 116.5 kB | 1 | 29-Apr-2025 16:00 | krivacsz | |
png |
get_acccess_token_variables.pn... | 121.1 kB | 2 | 30-Apr-2025 05:41 | krivacsz | |
png |
get_access_token_http_1.png | 121.5 kB | 1 | 29-Apr-2025 16:08 | krivacsz | |
png |
get_access_token_http_2.png | 46.3 kB | 1 | 29-Apr-2025 16:12 | krivacsz | |
png |
get_site_permission_http_1.png | 109.0 kB | 1 | 29-Apr-2025 16:27 | krivacsz | |
png |
get_site_permission_http_2.png | 45.5 kB | 1 | 29-Apr-2025 16:29 | krivacsz | |
png |
grant_sharepoint_site_access_j... | 249.2 kB | 3 | 30-Apr-2025 07:18 | krivacsz | |
xml |
job.XML | 47.3 kB | 1 | 01-May-2025 04:57 | krivacsz | |
png |
new_permission_http_1.png | 116.3 kB | 1 | 30-Apr-2025 07:03 | krivacsz | |
png |
new_permission_http_2.png | 51.7 kB | 1 | 30-Apr-2025 07:09 | krivacsz | |
png |
new_permission_related_variabl... | 125.4 kB | 1 | 30-Apr-2025 06:59 | krivacsz | |
png |
parse_access_token_from_respon... | 86.0 kB | 2 | 30-Apr-2025 06:18 | krivacsz | |
png |
site_selected_microsoft_graph.... | 170.2 kB | 1 | 30-Apr-2025 02:38 | krivacsz |
«
This particular version was published on 30-Apr-2025 07:56 by krivacsz.
G’day (anonymous guest)
Log in
JSPWiki