Azure Files: Link
!!!! General restrictions: Azure Storage is not a traditional file system but an object storage service. What appears to be a folder is actually just a prefix in the object’s name. As a result, renaming folders is not supported. To move a folder, you must copy all the objects to the new location and then delete them from the original one.
!!! Proxy Configuration: If your server accesses the internet through a proxy, make sure to whitelist the following domains to allow Azure API access:
• file.core.windows.net or file.privatelink.core.windows.net
• blob.core.windows.net, blob.core.chinacloudapi.cn or blob.privatelink.core.windows.net
1. Azure File Share
#
CrushFTP supports Microsoft Azure Shares as a VFS item, it requires a Storage Account: Storage account overview Link
 .
.More Info: Azure File Share Link

The URL should follow this structure (replace the placeholders with your actual values):
azure://STORAGE_ACCOUNT_NAME:ACCESSKEY@file.core.windows.net/SHARE_NAME/
azure://STORAGE_ACCOUNT_NAME:ACCESSKEY@file.privatelink.core.windows.net/SHARE_NAME/
You can find the required details in the Azure Portal. Navigate to your Storage Account, then select Access keys from the left-hand menu to view the credentials.
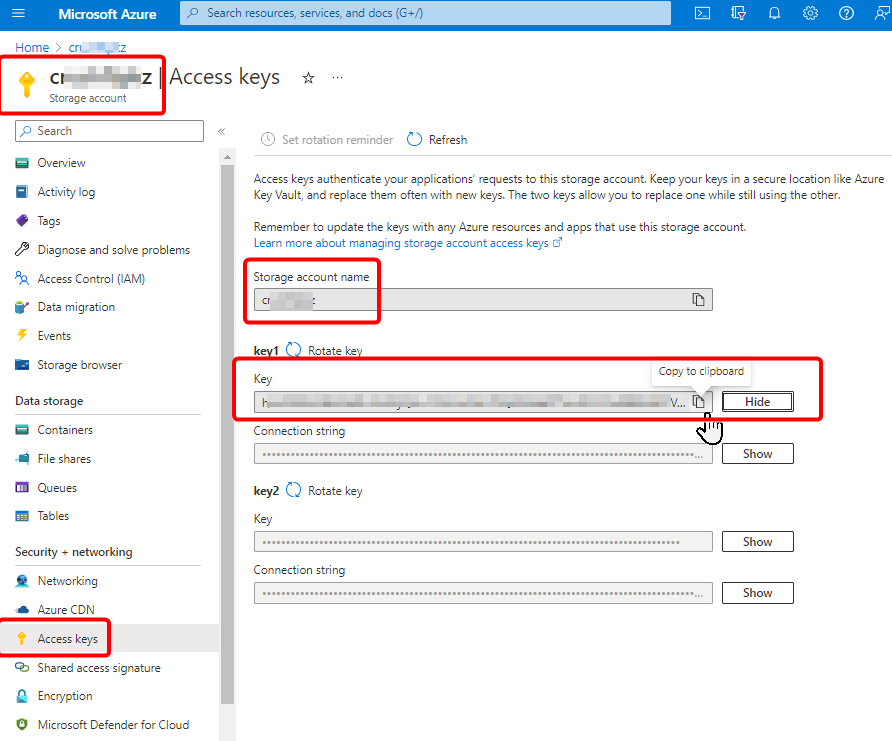
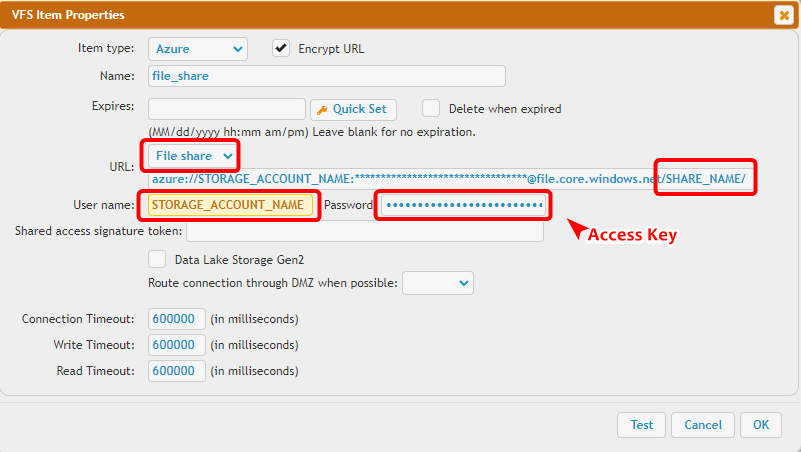
Provide the Storage Account name as the Username, and the Access key as the Password in the VFS item’s Properties section.
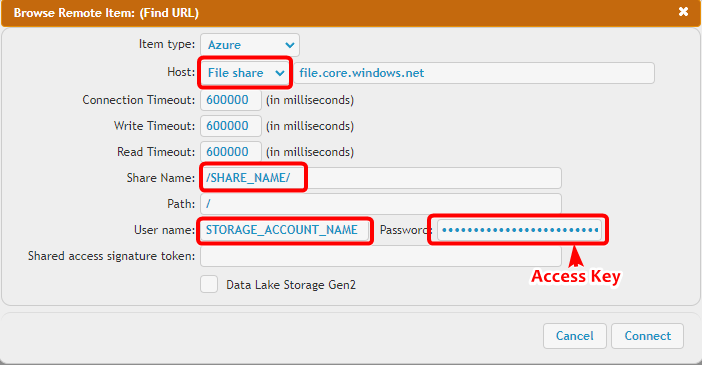
When using the Browse… option in the Jobs interface or plugin interfaces, the user interface differs slightly:
There is an input field specifically for the file service share, labeled Share Name.
2. Azure Blob Container
#
CrushFTP supports Azure Blobs (Introduction to Azure Blob Storage Link
 ) as VFS item, it requires a Storage Account: Storage account overview Link
) as VFS item, it requires a Storage Account: Storage account overview Link .
.The URL should follow this structure (replace the placeholders with your actual values):
azure://STORAGE_ACCOUNT_NAME:ACCESSKEY@blob.core.windows.net/BLOB_CONTAINER_NAME/
azure://STORAGE_ACCOUNT_NAME:ACCESSKEY@blob.core.chinacloudapi.cn/BLOB_CONTAINER_NAME/
azure://STORAGE_ACCOUNT_NAME:ACCESSKEY@blob.privatelink.core.windows.net/BLOB_CONTAINER_NAME/
Data Lake storage Gen2: More info on the official website: Data Lake Storage Introduction Link
 .
.Turn on the flag if the storage type is the data lake. It connects using the Azure Blob Storage REST API ( More info: Blob Service REST API Link
 ), but does not support the Azure Data Lake Storage Gen2 REST API. (More info: Azure Data Lake Storage Gen2 REST API Link
), but does not support the Azure Data Lake Storage Gen2 REST API. (More info: Azure Data Lake Storage Gen2 REST API Link )
)When using the Browse… option in the Jobs interface or plugin interfaces, the user interface differs slightly:
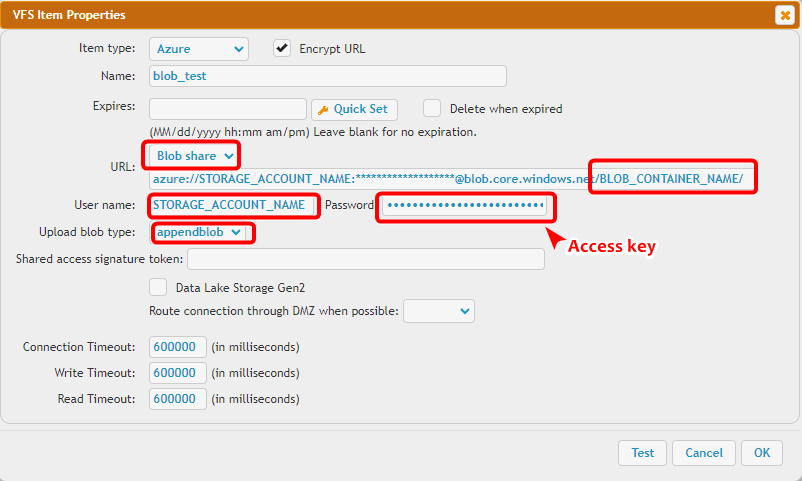
To specify the Blob Container, use the Share Name input field.
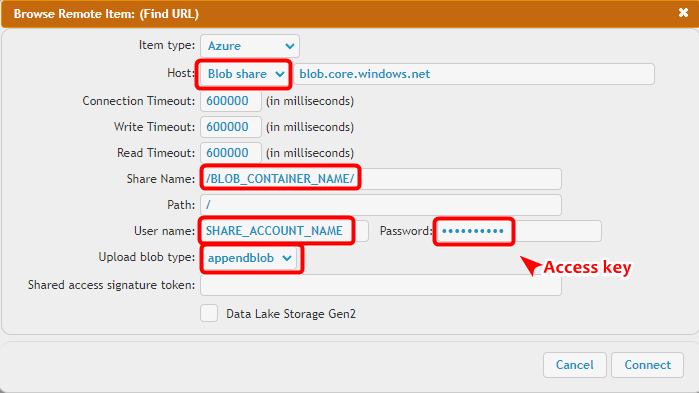
You need to select the blob type (append blob or block blobs - page blobs are not supported) specified when creating the blob on Azure.
3. SAS token
#
Azure also can delegate access with a shared access signature (SAS) https://learn.microsoft.com/en-us/azure/storage/common/storage-sas-overview
 .
.In this case, the URL should look like:
azure://STORAGE_ACCOUNT_NAME:@blob.core.windows.net/BLOB_CONTAINER_NAME/
Or
azure://STORAGE_ACCOUNT_NAME:@file.core.windows.net/SHARE_NAME/
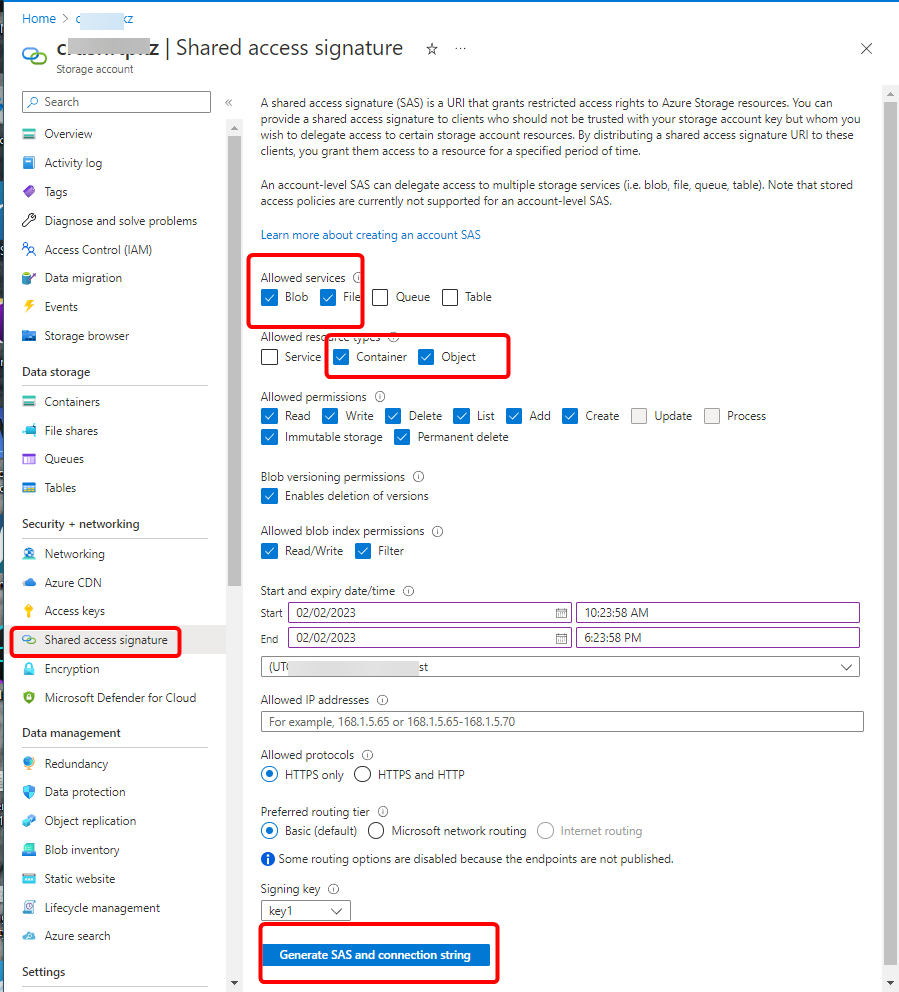
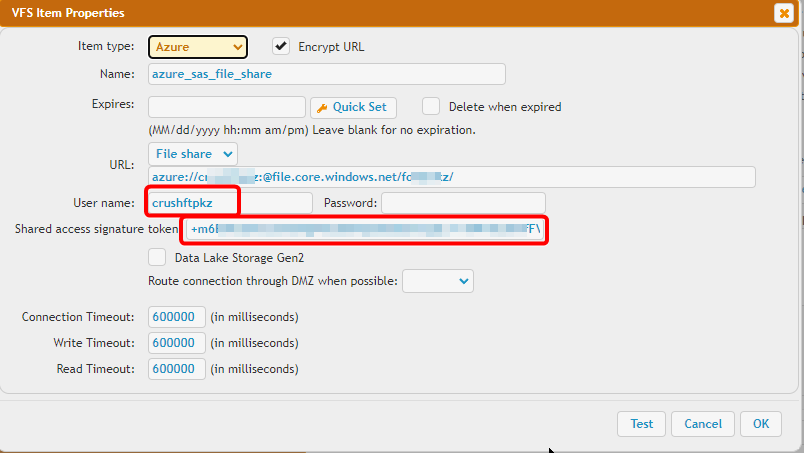
The password field should be empty and put the SAS token to the "Shared access signature token" input field.
4. Authorize access to blobs using Microsoft Entra ID
#
Azure Storage supports using Microsoft Entra ID to authorize requests to blob data. (see more info : https://learn.microsoft.com/en-us/azure/storage/blobs/authorize-access-azure-active-directory
 )
)You will start at the Microsoft Azure portal:
https://azure.microsoft.com/en-us/features/azure-portal/

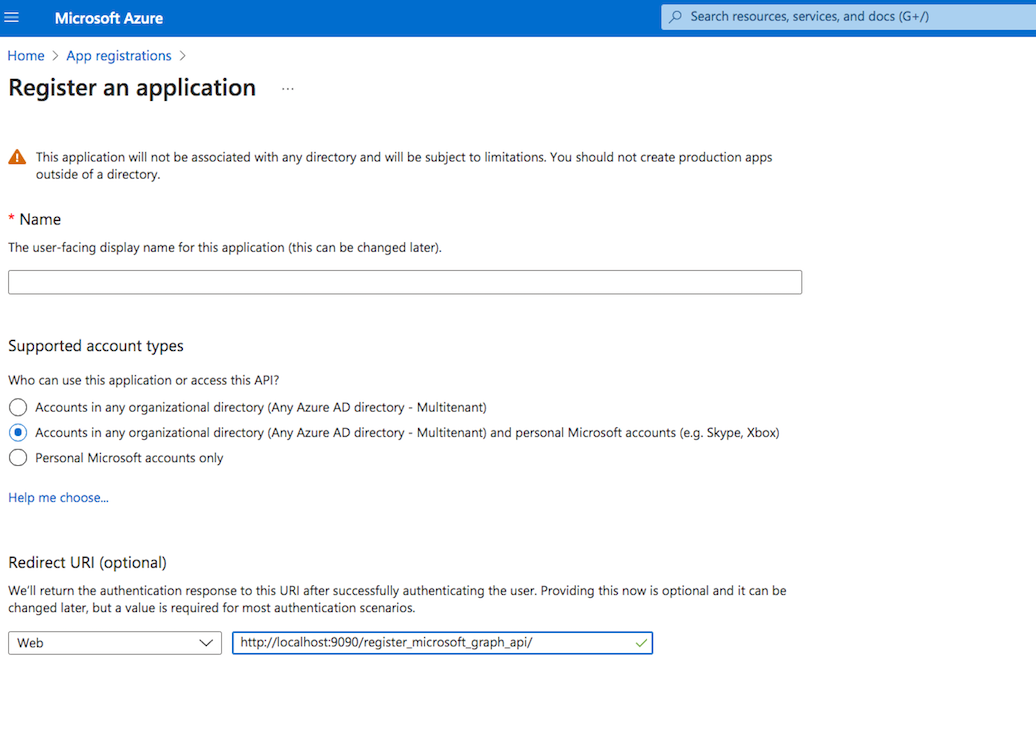
Application registration: Go to the App registrations and click on New registration:
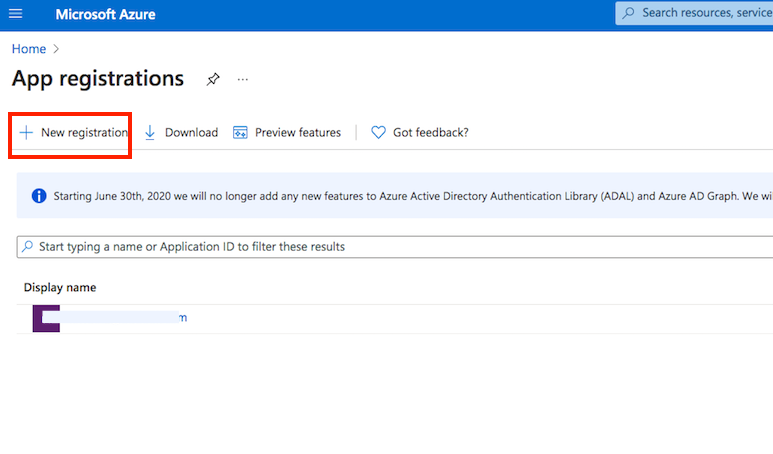
Name it. Select the Microsoft account types. The redirect URL must end with "register_microsoft_graph_api/". Then click on register.
http://localhost:9090/register_microsoft_graph_api/
Under the redirect URL configuration enable the Access Token to be issued by the authorization endpoint:

Configure the API permissions:
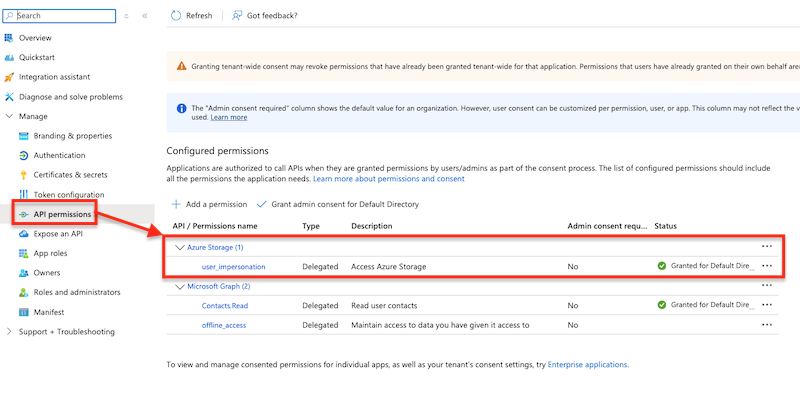
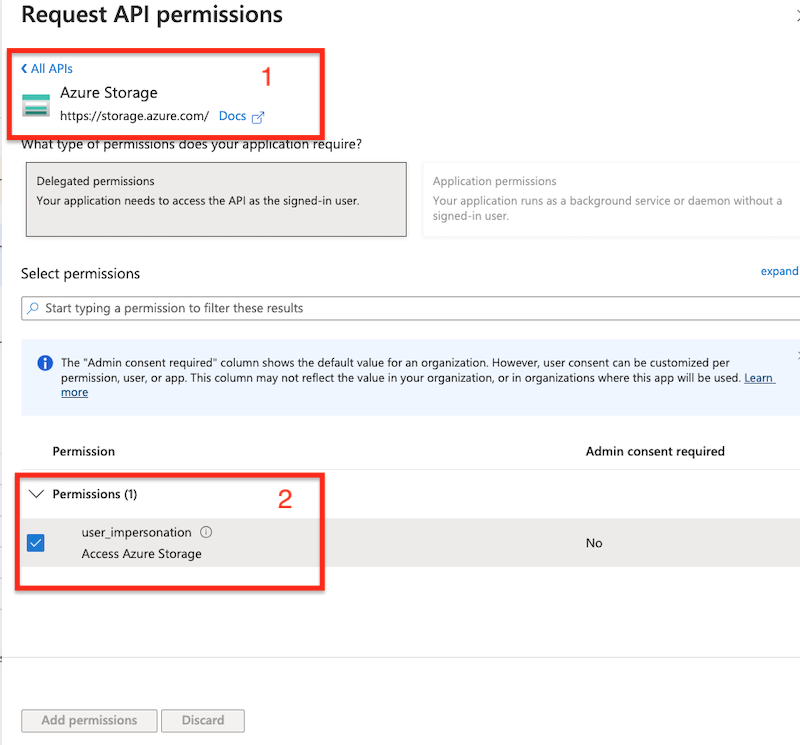
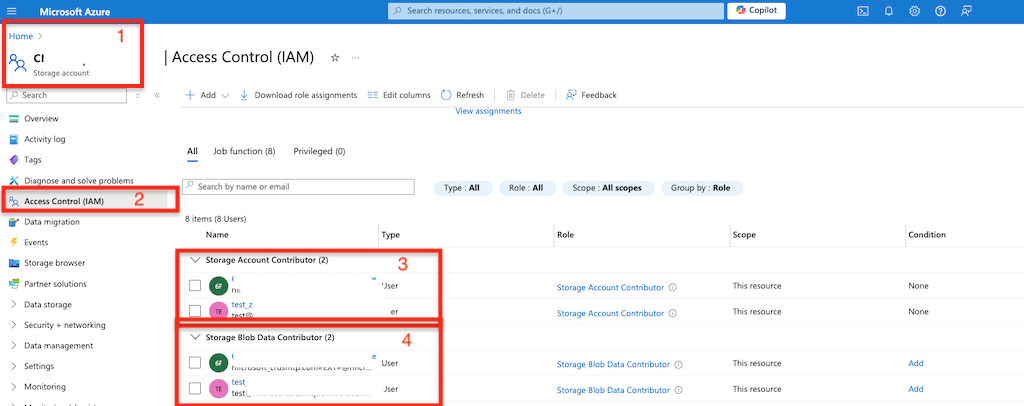
On your Storage Account at Access Control (IAM) assign the role "Storage Account Contributor" and "Storage Blob Data Contributor" to the specified user.
Restriction: It only works with blob storage.
Access the user's VFS settings and configure the Refresh Token for the remote Azure connection. At User Delegation Settings click the "Get Refresh Token" button.
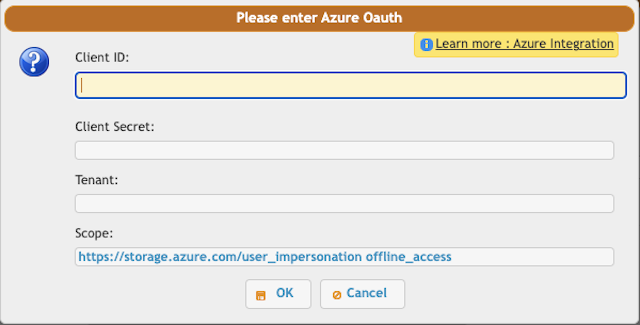
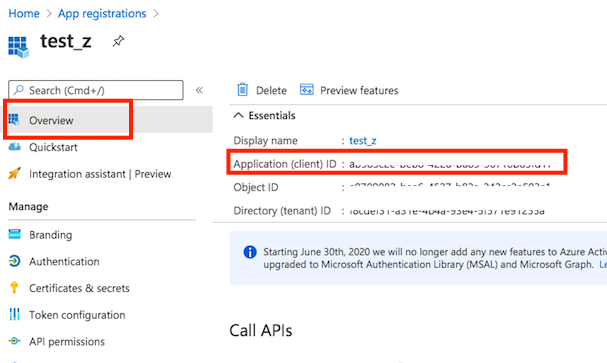
Client id : You can find it at Azure portal -> App Registration -> Overview:
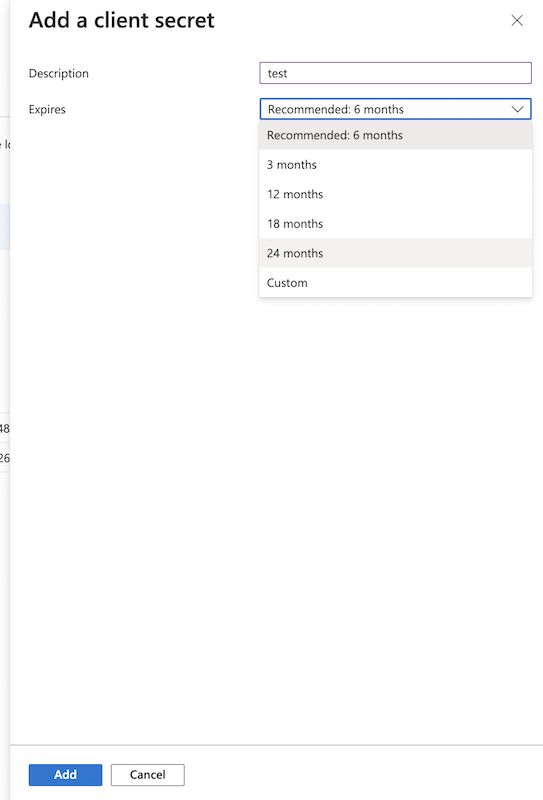
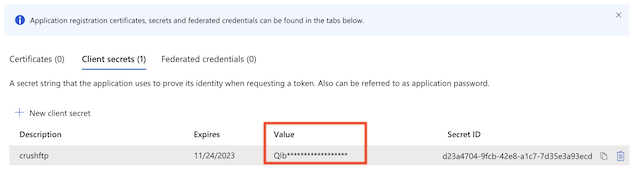
Secret key: A new client secret also needs to be created. Go to the "Certificate & secrets" and generate a new secret key. Click on New client secret.
Sign in as the specified Microsoft user grant access, and obtain the refresh token.
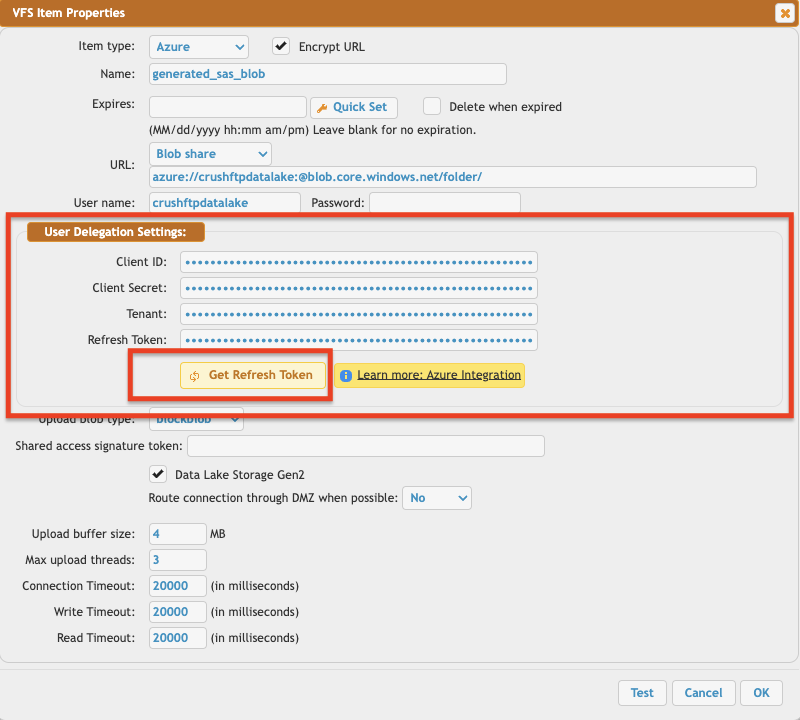
!!!Provide the storage account name as the "User name" input field.
To get a newly created SAS token for your storage, you need to run the following job example: CrushTaskExample18
Add new attachment
List of attachments
| Kind | Attachment Name | Size | Version | Date Modified | Author | Change note |
|---|---|---|---|---|---|---|
png |
AzureConfiguration.png | 78.7 kB | 3 | 05-Dec-2023 05:32 | krivacsz | |
png |
AzureConfiguration2.png | 77.5 kB | 3 | 05-Dec-2023 05:32 | krivacsz | |
png |
AzureConfiguration3.png | 27.4 kB | 3 | 05-Dec-2023 05:32 | Sandor | new UI elements |
png |
AzurePortalAccessKey.png | 57.7 kB | 2 | 05-Dec-2023 05:32 | Sandor | blurred more |
png |
SAS.png | 97.0 kB | 1 | 05-Dec-2023 05:32 | Sandor | |
png |
Screen Shot 2017-08-09 at 9.08... | 113.4 kB | 1 | 05-Dec-2023 05:32 | krivacsz | Azure configuration |
png |
azureRemoteItem.png | 57.5 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
azureRemoteItem2.png | 53.5 kB | 2 | 05-Dec-2023 05:32 | krivacsz | |
png |
azureRemoteItem3.png | 20.3 kB | 2 | 05-Dec-2023 05:32 | Sandor | new UI elements |
png |
azure_VFS_SAS.png | 26.4 kB | 1 | 05-Dec-2023 05:32 | Sandor | |
png |
azure_access_control_roles.png | 132.8 kB | 1 | 07-Oct-2024 04:38 | krivacsz | |
png |
azure_api_permission_blob.png | 130.2 kB | 1 | 07-Oct-2024 04:17 | krivacsz | |
png |
azure_blob.png | 74.0 kB | 3 | 05-Dec-2023 05:32 | krivacsz | |
png |
azure_blob3.png | 29.6 kB | 4 | 05-Dec-2023 05:32 | Sandor | new UI elements |
png |
azure_blobRemoteItem.png | 21.5 kB | 4 | 05-Dec-2023 05:32 | Sandor | new UI elements |
png |
azure_refresh_token_form.png | 48.4 kB | 1 | 07-Oct-2024 04:50 | krivacsz | |
png |
azure_user_impersonation.png | 152.5 kB | 1 | 07-Oct-2024 04:17 | krivacsz | |
png |
user_delegation_settings.png | 94.4 kB | 2 | 07-Oct-2024 04:49 | krivacsz |